Deception ICS

During this article, It will talk about how to protect our industrial control systems (ICS) against advanced cyberattacks: deception systems. This innovative form of protection revolutionizes conventional measures through proactive protection. During the development of this article, we will investigate its functioning and objective, analyzing its role in ICS and its current application.
What are SCI deception systems?
The Concept of Cyber Deception was first introduced in 1989 by Gene Spafford, with the aim of referencing a type of active defense against possible incidents.
SCI Deception Systems, are services that improve the early detection of intrusions, through the implementation of distraction and delay mechanisms for cybercriminals, increasing the margin to be able to apply incident procedures early.
One of the great drivers of this type of system, This is the virtualization technologies that have allowed the implementation of new solutions to deal with increasingly sophisticated attacks, such as honeypots. These consist of a virtualized environment parallel to the real production environment, allowing the organizations to confuse attackers about what the real environment is and how to secure depending on the techniques used by attackers in the systems.
With the passage of time, more advanced technologies emerged, such as deception platforms, considered as an evolution of honeypot systems, applying analytical intelligence according to the behavior of malicious actors.
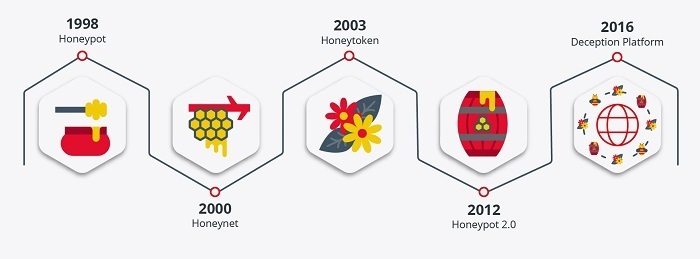
- Evolution of technologies to deceive attackers. Source. -
Today's deception systems consist of the creation of a virtual environment, additional and parallel to the real production environment. Detection and analysis systems are added to this environment, which normally reproduces the real ICS to be protected in the virtual world, to obtain information on the activity of the attackers on the system. In this way, these devices give time to react to intrusions in real production environments.
Currently, the use of this type of system is more widespread in IT environments, as they tend to be easier to virtualize and more homogeneous among them. However, they are already being adopted in OT environments, coinciding with an increase in the adoption of virtualization technologies in OT environments where scalability, flexibility and cost reduction are paramount.
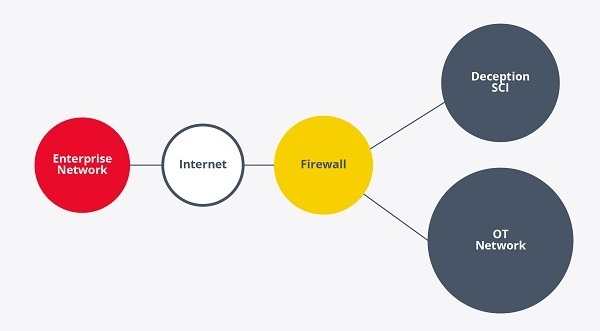
- High-level infrastructure for the deployment of deception systems. Source. -
Application in Industrial Control Systems
Today, security in ICS is usually governed by international standards. There are a multitude of them, depending on production sectors or types of ICS, such as ISA99, IEC 62443, NIST, which provide security guidance and best practices for the implementation of security solutions in industrial environments. This type of standard is generally based on a defense-in-depth model, which involves using different consecutive layers of security controls to protect IACS (Industrial Automation and Control Systems).
Deception systems, in general, do not aim to present a global solution to replace these more traditional defense systems. Instead, they work directly with traditional defenses to improve protection against potential threats.
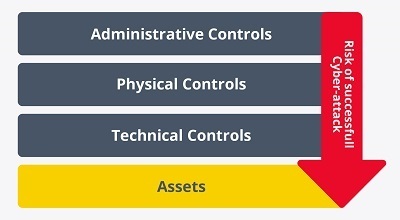
- Risks of a cyberattack achieving its goal. Source. -
The main function of the duplication of the real system that is performed in deception systems is to present themselves to potential attackers as the real environment they want to access and exploit. To this end, hybrid systems have also been developed, which use real OT equipment together with virtualized elements, to obtain greater credibility and compatibility with these systems.
In general, these environments are usually located at level 3 of the Purdue model, which usually serves as a boundary between IT and OT environments. This gives them more credibility, since it would be normal for an ICS to have a connection at this level, and at the same time isolates them from the real environment to avoid creating a possible attack vector.
How does an SCI deception system work?
The goal of deception systems is to confuse the attacker, preventing them from differentiating between real ICS and implanted deceptions. Its operation consists of the use of tactics and techniques, collected by the methodology MITRE D3FEND and its application serves two main functions: delaying attackers to allow more response time, and generating intelligence on attackers' behavior based on their actions in the simulated environment. Although, currently, there are a myriad of tactics and techniques that could be implemented, some of the most common are:
- Most commonly used tactics:
- Decoys or honeytokens: this type of tactic consists of distancing the attacker as much as possible from the network we want to protect, providing them with false information, allowing us to redirect and monitor the progress of malicious actors. For example, by publishing manipulated architecture diagrams to databases on more accessible networks.
- Fake network traffic: This type of tactic involves creating traps and decoys on the network with false information, with the aim of camouflaging real sensitive data. For example, by injecting orders or production history from the simulated environment into the real network, confusing a potential attacker.
- Most commonly used techniques:
- Medium Interaction Decoys: This type of technique acts as a reaction to certain actions of the attacker and offers a particular pre-programmed response to said interaction. For example, by using an FTP service that, depending on the attacker's behavior, activates certain services and continues to collect information from the attacker.
- High Interaction Decoys: This technique is a more advanced version of medium interaction decoys, based on presenting a more complex reaction to the attacker, through advanced scripting or even manual action by the monitoring team. For example, changing the operation of the simulated plant as the attack progresses, applying the realistic response procedures that would be applied in the real environment to check its efficiency against the attacker.
Although different services are usually deployed according to the behaviors that is expected from the attacker, it is not necessary to create a system from scratch for each specific case. Another option is the use of existing honeypots for SCI which, although they may be easier to identify by an advanced attacker, can be a useful and easy-to-use tool to gain insight into the general behavior of an attacker on our system. For example, these are some of the honeypots that are commonly used in OT environments:
- Conpot is an open source honeypot that supports several industrial protocols (IEC 60870-5-104, BACnet, Modbus, s7comm) and other well-known protocols (HTTP, SNMP, and TFTP).
- XPOT: is a honeypot that allows you to simulate a PLC. It is a software-based system and allows high interaction between the user and the attacker, allowing, for example, to compile, interpret and load PLC programs in the honeypot. It supports both S7comm and SNMP protocols. It can simulate the operation of Siemens S7-300 PLC.
- CryPLH: is a virtual ICS honeypot that allows you to simulate Siemens PLCs (S7-300). It works by using a Linux-based host and MiniWeb HTTP servers to simulate HTTP or HTTPS, a Python script to simulate the ISO-TSAP protocol, and a custom SNMP implementation.
Advantages and disadvantages
In today's industry, the emergence of new technologies that allow us to improve or change our environment is constant and exponential. Deception systems are just one of the latest examples of protection technologies at our disposal. And, like all cutting-edge technologies, they have a series of advantages and disadvantages associated with their implementation within the OT world.
- Advantages:
- increased visibility in the event of cybersecurity incidents.
- improved threat detection.
- lower rate of false intrusion warnings.
- better response to a cybersecurity incident.
- Disadvantages:
- increased complexity of implementation and maintenance.
- increased exposure to potential vulnerabilities.
- the need for a high level of cybersecurity maturity.
- difficulty virtualizing OT environments.
Conclusion
In recent years, cyber incidents in industrial environments have increased considerably. All of these attacks can have a high impact on the organization, making them a target for attackers. For this reason, the use of increasingly advanced and efficient protection technologies is a necessity in industrial environments. Among these, deception systems are a powerful tool to develop a response plan to multiple types of incidents, allowing detection, monitoring, intelligence generation and development of more advanced incident response procedures.
On the other hand, it is important to mention that these systems require a high level of cybersecurity maturity in our industrial environment. In addition to mature virtualization capabilities. These requirements are imperative for our deception system to be effective and for us to be able to leverage the valuable information it provides us to protect our real ICS.
In short, ICS deception systems allow an additional layer of security to be applied in parallel to the usual defense-in-depth model. Well applied and managed, they can act as a time buffer between the start of an attack and the response, as a research tool to develop a more efficient and effective protection system or even as a testing environment for new changes in our environment where virtual environments have already been incorporated.









