PLCs security risks

During 2022, Spain was the fourth European country with the most cyber-attacks on industrial control systems and more than 40% of OT (Operational Technology) systems were affected by malicious software during that same year.
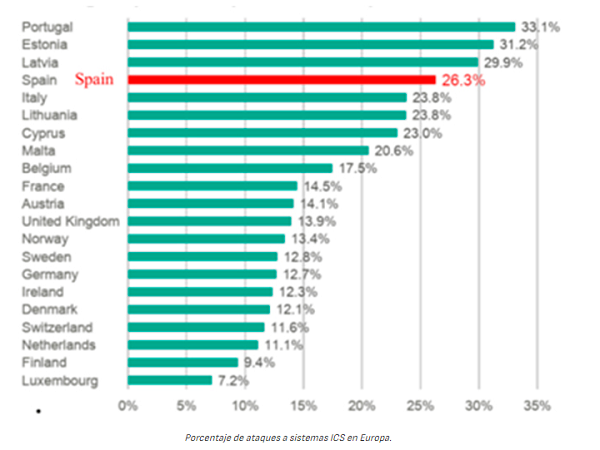
- Percentage of ICS attacks in Europe -
This trend is in addition to the exponential increase in the adoption of new technologies aimed at improving productivity or management of industrial environments. However, with widespread adoption, inherent risks arise that reduce the security of our environments if they are not implemented correctly. To help in this regard, this article will explore the risks associated with PLCs, one of the most critical devices in the industrial environment, and the importance of addressing those risks.
What are the phases of a cyber-attack on a PLC?
Although the phases of an attack may vary from case to case, in general it is possible to identify some basic steps through which attackers usually advance:
- Access: the first phase in gaining remote access to the PLC network of an industrial plant. It is important to establish architectures that implement security in depth, so that to gain remote access to PLCs it is necessary to pass through several security points, reducing the risk that an attack can reach the following phases.
- Discovery: this stage consists of gathering information on the PLCs used by the target, their configuration, security measures and communications used to perform their functions. To do this, attackers usually use espionage and reconnaissance techniques, identifying industrial protocols, equipment models and brands, attack vectors and critical points in the infrastructure. To make this phase more difficult, it is important to properly bastion our PLCs (restrict access to configurations, encrypt communications, change default access...) and keep the production network monitored. The more time and effort the attacker needs to identify attack vectors, the more likely he will be detected in the process.
- Control: this phase consists of gaining access to the PLC configuration. This may require something as simple as using default credentials, to more complex techniques such as exploiting security vulnerabilities in outdated equipment. Once inside, the attacker can gain full knowledge of the PLC operation, spread to other equipment more easily and gain persistence in our network.
- Damage or Impact: in this phase, once control has been acquired, the attacker will move on to the attack itself. A PLC is a critical target for an attacker, from here he can go on to leak confidential information about the production process, alter the process by sending unauthorized commands to the actuators, falsify sensor readings and databases or directly disable the equipment and stop production.
- Obfuscation: in this phase unlike an IT cybersecurity incident the goal is usually not to hide the attack itself, as most OT impacts are visible. The priority in this case is to hide the techniques used and the extent of the attack so that, ideally, the computers can be re-infected once they have recovered.
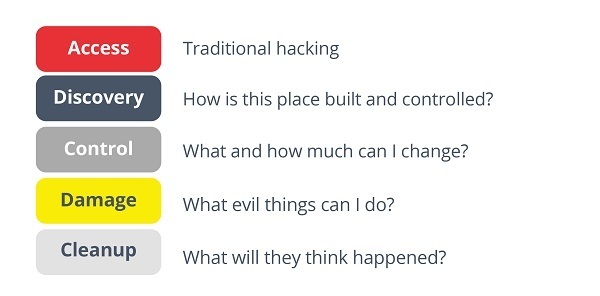
- Phases of attack on a PLC. Source -
What are the effects of a cyber-attack on a PLC?
Nowadays, modern industrial plants face multiple challenges and changing conditions (product delivery, product quality, costs, environmental standards...), therefore, the adoption of flexible and adaptable systems has become increasingly important.
In industrial environments, unlike in IT environments, where the main objective is usually confidential information, the priority is usually to compromise the availability of the control system, stopping plant production.
There are different effects that an attack can have on our ICS:
- Damage to equipment: this type of cyber incident aims to cause to the system, equipment or industrial plant. There are multiple ways in which a malicious actor who has taken control of the ICS can attempt to damage industrial equipment, for example, by:
- Equipment stress: accelerating the normal gradual wear and tear that industrial equipment undergoes during operation. With this objective in mind, an attacker can alter the PLC configuration to repeat unnecessary movements or to facilitate the appearance of faults or failures in the infrastructure.
- Manipulation of equipment safety limits: safety limits controls that variables (temperature, speed, pressure...) do not reach dangerous values. But an attacker could modify these values in the PLCs belonging to the safety systems of an ICS allowing them to reach unsafe values for the operability of the system.
- Damage to the production process: another possible vector of attack is the quantity, quality, or cost of production:
- Product quality and production rate: this violation targets the final product. It usually consists of compromising the integrity of PLCs, modifying their configuration with the aim of worsening the overall quality of the products or the rate of valid products produced, resulting in reputational damage, economic damage, or even legal compliance consequences.
- Operational costs: this vulnerability consists of modifying the integrity of the PLC configuration in a way that incurs additional costs. By altering waiting times, target temperatures or mixing percentages, an attacker can increase our energy, materials, fuel, etc. costs. Although initially a minor cost, this attack can extend over time, incurring considerable expense.
- Legal consequences: this type of violation may affect the company's ability to comply with the stipulated regulations.
- Safety: This type of violation is aimed at PLCs responsible for the safety of company personnel and/or third parties. In addition to legal sanctions, the malfunctioning of this equipment can cause occupational accidents or collateral damage.
- Environmental impact: more and more industrial sectors are subject to strict environmental regulations and demanding sustainability objectives. These types of violations target a company's ability to meet these requirements by falsifying PLC measurements or control of emission control, water purification, material recycling and other processes essential to controlling the company's environmental impact.
- Contracts: whether it is service contracts, required quality levels or order fulfillment, an attack on our plant's ICS can compromise our ability to fulfill contracts with our customers. Breaching these agreements as a result of a cyber incident can lead to legal penalties, reputational damage and put third parties at risk.
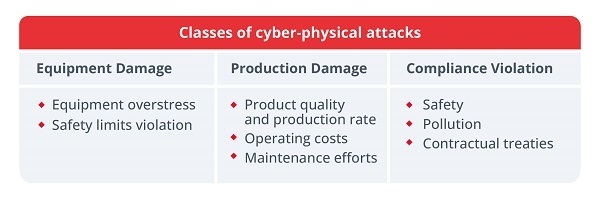
- Types of physical cyber-attacks. Source -
How to perform the expertise of a PLC after a cyber-incident?
The objective of PLC expertise is to evaluate and study, in case of a cyber incident, what would be the causes and its origin. This process must be carried out by specialized personnel, normally industrial engineers specialized in industrial electronics or in the sector relevant to the affected company and certified for this type of project.
In the forensic analysis, conclusive evidence of unauthorized manipulation of the ICS is sought. Specialized tools are used for this purpose, e.g. Microsoft ICS Forensics Framework, a widely used tool for forensic analysis of PLC metadata.
This tool runs under Python and is open source. Its operation consists of obtaining information from a configuration file, introducing queries to the application. This application obtains the answer from the metadata stored in the PLC plugins, obtaining the requested data (type of machine, last productions, active process...).
- Microsoft Forensic Tools. Source -
What cybersecurity standards can be used to protect a PLC?
The most widespread and accepted standard for ICS protection is the IEC-62443 standard framework. This is divided into four cybersecurity domains aimed at overall security, from the management level of enterprise management to the operation of each device:
- General: general cybersecurity framework of the company. How responsibilities, procedures and security systems will be organized and managed.
- Policies and procedures: how to create, manage and apply policies and procedures and which ones we need to implement.
- Systems: how the systems that make up our process should be designed to achieve the target security level.
- Components: how individual equipment and components of our systems should be configured and protected.
Within each domain, IEC-62443, there are multiple standards focused on the aspects of cybersecurity relevant to it. Each standard defines a set of requirements with different levels of compliance. In this way, users can identify the overall maturity of their company, define a target level, and apply the necessary requirements to achieve it.
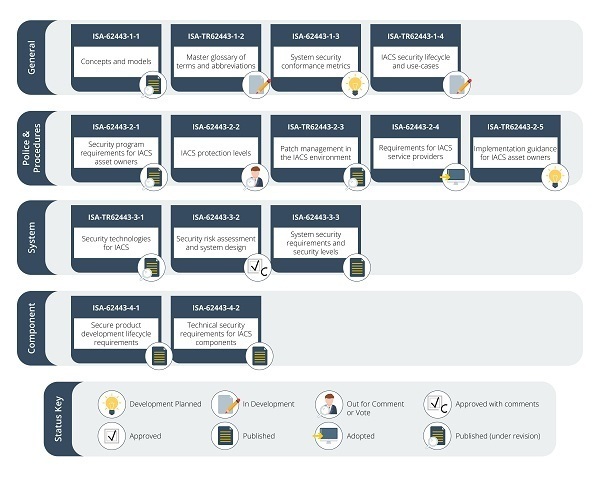
- IEC 62443 family of standards. Source -
For cybersecurity in PLCs, the use of standards 62443-4-1 and 62443-4-2 is recommended. The particularity of this equipment as long-lived devices, difficult to maintain, but with a critical role in industrial systems, highlights the need to know and apply these types of standards, which can serve as a basis and guide to reduce cybersecurity risks.
Conclusions
Industrial companies depend on their ICS for their daily operations and PLCs have always been the basic tool of which they are composed. These devices are one of the differentiating elements of OT environments and have always used specific technologies and techniques, from proprietary communication protocols to operating systems and specific firmware. This has kept them out of cyber-attacks for some time, as they presented a technical challenge that attackers did not see the need to embark on, being able to focus on more familiar IT environments.
However, recently, the evolution of threats and the combination of IT and OT environments has changed this paradigm. PLCs are more accessible and vulnerable to cyber-attacks, which has led to the creation of specific attack techniques and specialized regulations to counter them.
Given the criticality of this equipment in our industrial networks, it is necessary to know the standards and best practices that can guide us to reduce and eliminate increasing risks. Protecting, basing, and properly managing our PLCs and industrial control systems is essential to ensure that our process can operate safely and meet our business objectives.









