
UMAS (Unified Messaging Application Services) is a Schneider Electric (SE) proprietary protocol used to configure and monitor Schneider Electric programmable logic controllers (PLCs). While it is true that the protocol is related to this manufacturer, the use of the protocol is quite widespread in different sectors, especially the energy sector, as is obvious.
The article will focus on the technical breakdown of the protocol and the use of the protocol. The article will also show weaknesses, strengths and some technical vulnerabilities detected in this protocol.


In the electricity sector, it has always been necessary to use robust communications that allow proper communication, since a failure in this sector would cause a large number of losses, both economic and social.
In addition, with the technological advances, it is important also to have secure communications since the electricity sector is one of the sectors that currently suffers the most cyber-attacks. For this reason, in recent years different robust and secure protocols have been created.
One of these protocols is DNP3, created mainly for the use of substation automation and control systems, for the electric utility industry, although it has now also been used for other sectors.
Finally, in this article we want to explain in more depth the operation of this protocol and the benefits or disadvantages of using this protocol.

The automotive world has always been one of the most cutting-edge sectors in terms of the technology used, which is why today's cars are equipped with technologies such as Bluetooth, NFC, GPS, etc., which improve different aspects such as comfort, fuel efficiency and increased safety.
But these implemented technologies can also bring with them serious problems, such as the risk of cyber-attacks that can affect passengers in the vehicle, both at the level of personal data and physical security.
For this reason, this article aims to provide an insight into some of the cyber-attacks that smart cars have suffered and how cyber-security is evolving and adapting to make more and more vehicles cyber-safe.

The industrial environment, especially the energy sector, is one of sectors that is suffering the most from cyber-attacks. This trend has been increasing in recent years, as this is one of the most information-sensitive sectors and can cause major problems, both economically and socially.
One of the best examples of malware attacks is BlackEnergy. This malware became known for being able to compromise several electricity distributors on 23 December 2015, causing households in the Ivano-Frankvisk region of Ukraine (a population of around 1.5 million) to be without electricity.
For this reason, due to seriousness of this type of cyberattacks, it is necessary to continue researching and investing in industrial cybersecurity, to reduce the damage caused by this type of cyber-attack in industrial environments.

The automotive sector is currently moving towards electric consumption, as society is becoming more and more aware of the problems that environmental pollution can cause.
One of the big challenges of this trend is how to charge electric vehicles, for which charging points are currently used.
But like most of today's technological devices, they will also need to have access to an Internet connection in order to be able to monitor in real time the use of the station, the customer's banking information, etc.
For this reason, in this article we want to talk about the different risks or cyber-attacks that these charging points may suffer and the problems they may cause, as this is a very important sector for society and one that is capable of managing very sensitive information

The increase of malware specifically designed to run on systems that support industrial processes creates a need in the industry that can be partly covered by different technological solutions. This article will focus on the different options available on the market to detect malicious files that aim to modify the operation of industrial environments or simply cause denials of service.
Both portable and agent-deployed solutions can be an option, and this article will reflect on these and other options as well as provide guidelines on when it is best to use one solution or the other.
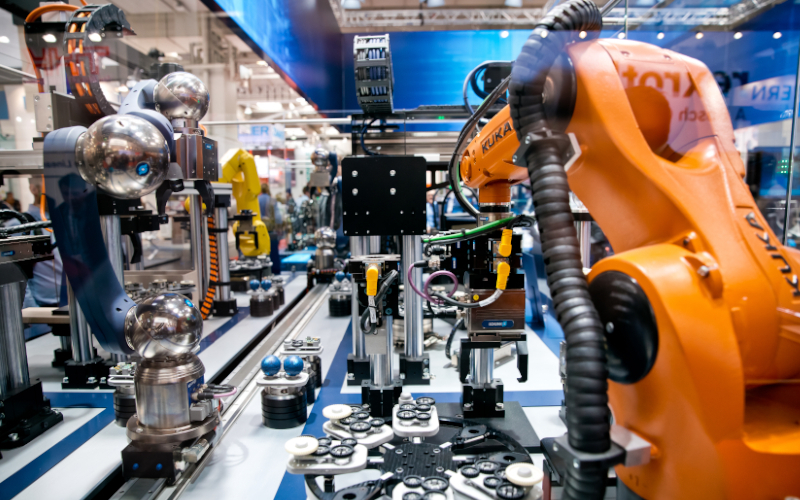
Within the industrial world, there are some sectors such as robotics, which has evolver considerably. This has led to the need to update all the regulations and standards, both in terms of physical (safety) and cybersecurity. (security). Given that the robotics sector is and will increasingly become a highly technical sector with exponential growth, the need to update all documentation has been promoted by a large group of companies in the sector, which, above all, have focused their concerns on the cybersecurity of the industrial robotics world.

The proliferation of cybersecurity incidents in industrial environments has given rise to a huge concern in the various existing sectors. Some of them, such us the energy sector, are choosing the path taking in the banking sector with the TIBER-EU framework. In addition, many governments are allocating large sums of money to their government agencies to develop strategic plans in which that exercises are included

Confrontations between countries no longer only take place in the physical world, in this new decade, these confrontations also move to the cyber world. The conflict between Russia and Ukraine is one of the clearest examples. Among the events that have taken place is the security incident known as Industroyer2, which affected an electrical supplier in Ukraine. The Industroyer2 is the evolution of its predecessor, the malware known as Industroyer, which was able to affect multiple protocols of industrial control systems during its execution. This new variant of the malware focuses on a particular communications protocol, IEC-104, which is widely used in Europe and the Middle East to monitor and control the power system via the TCP/IP communications protocol.



