Active defence and intelligence: from theory to practice

Nobody doubts that the defence of industrial facilities needs to be adapted to the new attack vectors. The evolution and sophistication of the attacks is more than evident, but the defence mechanisms have also evolved.
Knowing the new defence concepts, such as active defence or intelligence, is the starting point to understanding their implementation, without making certain classic mistakes with these terms due to lack of information, or what is most likely, the excess of information on this issue.
As it is normally understood, applied to the digital world, defence is based on a series of "defensive" actions undertaken with regard to an identified threat.
These actions can be categorised, much like many groups in cybersecurity, depending on the type of action, following one of the most accepted approaches that is displayed in the following image.
![]()
This type of very current and widely discussed approach may make more sense in IT environments, as when we transpose it into OT environments, not all the categories are valid.
"Offence" does not come into play with the word "defence", and less so in industrial environments. We will leave out that category and those associated words that may be all the range, such as "hack-back", "preventative hacking" and "counter hacking", etc.
It makes more sense to see defence in industrial environments and its current evolution in its pyramidal shape.

In said pyramid, the now consolidated foundations, both due to time and their level of implementation within the industrial control systems, can be identified:
- Secure architecture: within this category we find actions referring to secure network design, zones and conduits, good practice in networks (applying standards), both local and remote (manufacturers) access controls, etc.
- Passive defence: incorporates all elements of static defence (protection implemented without the need for human interaction). These actions include: IPS, AV, IDS, HIPS, etc.
The elements at the top of the pyramid, which will help to increase the level of defence, to adapt it to current needs and that should be the aim of implementing these in the near future, are:
- Active defence: including all the actions carried out by one or more trained people that are familiar with the infrastructure, aimed at identifying anomalies within the industrial network and taking determined measures in the face of these events.
- Intelligence: actions that make up part of the process of information gathering, interpreting this information and creating intelligence that is useful for the infrastructure. There is always human intervention when creating said intelligence.
Below, the previously outlined new defence challenges are explained in detail:
Active defence
We should be aware of the premise that there is not a one hundred percent effective defence. As well defined and implemented within the network architecture, based on good practice, as it may be, and regardless of the correctly configured passive defence mechanisms, there is still a small percentage of probability of an incident occurring, with this being considered as an anomaly in the normal working operations.
This is something that we should accept as a residual risk and we should not think of ourselves as being untouchable. Although all of these measures are going to filter the majority of attack attempts, or the least evolved ones, highly sophisticated attacks can evade the first two layers of the defence pyramid. It is here when active defence and intelligence really come into play as the next steps to increase the defence system's level of security.
When reference is made to active defence, it is applied to a whole process, not just a specific action. This is a constantly improving process, following a processing cycle through different essential phases. These do not follow a single categorisation, but rather they are specified in terms of the experience of the people involved in the industry security. By means of example, some of the phases that will definitely appear in all active defence cycles include:
- Observation/monitoring phase: One of the characteristics of the industrial sector, unlike with IT, is that it generates network traffic that tends to be constrained, specific and with repetitive actions, due to the fact that the logic programming tends to deal with clock cycles. All of this enables for the Network security monitoring tools to be boosted as much as possible. Monitoring the network traffic and correctly configuring the tools that enable the management and sending of the 'logs' generated by all the elements in our industrial network, as well as determining which alerts or events are generated, should be monitored and then handled. This is the basic process of this all-so-important phase in Active Defence. In short, the aim is to provide tools to identify and detect any anomaly within a specific industrial network.
- Detection response and reaction phase: This phase within active defence corresponds to the actions to be taken when an anomaly is detected. Within the industry, the main activity in this phase will be to maintain the control of the most risky elements, for example, starting to act at a manual level in certain devices. Although we should not forget that there is the aim of obtaining the most amount of forensic evidence, whilst putting measures in place to prevent dissemination. This is the most complicated phase, as it is undertaken in a state of alarm. As such, automating certain tasks may be a great help, for example, switching the monitoring systems to a state of "exhaustive monitoring" from the alert console may be extremely useful in an exceptional situation; as would registering everything and storing all the raw network traffic, if this was not previously being done, etc. In short, this phase encompasses the entire response operation to an anomaly: the control, search and actions to be carried out.
- Analysing what happened phase: This phase would include: a detailed analysis of everything obtained in the previous phase, an analysis of the traffic captured by the monitoring tools, of logs, of events, of samples found, etc. Furthermore, all of the corrective actions within the industrial environment and the creation of useful material must be taken into account; this prevents repeating the same mistakes (creating material to be consumed in the next phase).
- Learning or intelligence consumption phase: This phase, which many coin as 'Threat Intelligence Consumption', is essential within the active defence cycle, as it is going to offer more applicable defence mechanisms, provided that it is carried out correctly. The most complicated part of this phase is the capacity to implement measures extracted from the 'intelligence', whether this comes from ourselves or from external sources and, of course, the creation itself of this 'intelligence' in a format that is suitable to be consumed and applied in a specific industrial environment. Within this phase, for example, new YARA rules are applied, as are IoC and new firewall rules, remodelled for the environment or network, etc.
New phases within the active defence cycle have been defined, but they are not intended to be exact or unique, as previously mentioned, but rather they create a script upon which to act. However, they can be based on the experience of each industry and the elements that are available. Simply put, it is a pathway or work framework to be applied in the best possible way adapted to a specific environment.
Intelligence
The operation logic, data and information have their own meaning and they should not be confused, although the terms are often used alongside the concept of intelligence, which does make sense.
Intelligence is the result of a process, the final step of which must be carried out by an analyst. Tools make up part of this process, but they are never going to be capable of creating the intelligence for themselves.
In this intelligence creating process, the concepts of operation logic, also known as process data, environment data, information and finally, the creation of intelligence all appear. Data processing, both of the process and the environment, through different data analysis tools and techniques, will produce information. The interpretation by an analyst, who knows the industrial environment and its devices, of all the information obtained, and its correlation, as well as the creation and interpretation of hypothesis will create intelligence.
Visually, this process can be seen in the following image:
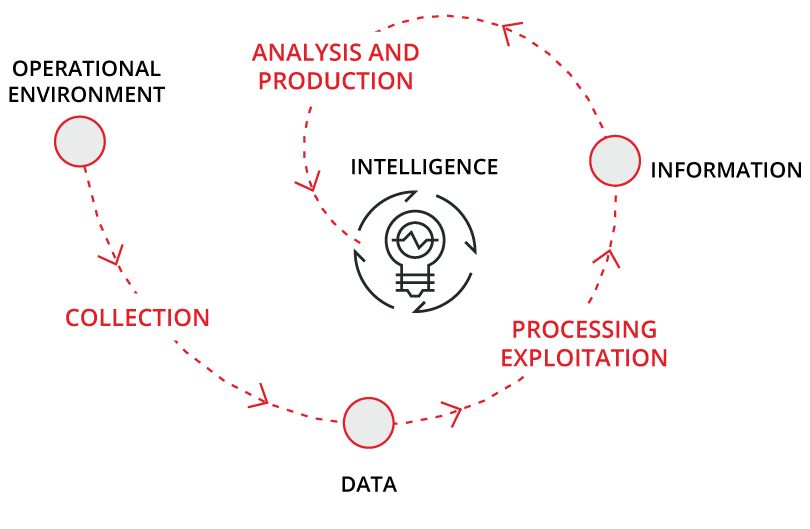
Applying intelligence aimed at a real risk analysis, training analysts, learning to identify other relevant sources of information, creating exchangeable objects of intelligence and many other actions will be part of the 'Threat Intelligence' orientated towards cybersecurity.
Active defence and intelligence are part of industrial defence these days; the days of waiting around for an attack to happen are over. The greater the capacity of detecting an anomaly in an industrial environment, and the shorter the time of adapting to an environment to offer a response to this anomaly, the greater the defence capacity. Training everyone involved is a fundamental element in order to be successful with regards to active defence. An anomaly may occur in any part of our industrial network and it should be detected by a tool or person at any level of said industrial network.









