Black Basta: response and recovery actions

The organized group of cybercriminals known as Black Basta, the name by which its own ransomware is also known, first emerged in the spring of 2022, operating under the ransomware-as-a-service (RaaS) model. This organization quickly established itself as one of the most prominent threat actors in the RaaS space globally.
Black Basta adopted the tactic of double extortion, characterized by the exfiltration of data prior to the deployment of the ransomware. The group was observed to operate through two portals on the Tor network; one dedicated to the dissemination of stolen information and the other to facilitate communication with victims.
Since its emergence, the group demonstrated considerable activity, particularly in the first months, managing to attack between 75 and 300 organizations, according to different sources, mainly in the United States, ranking as the fourth most prominent ransomware actor, in terms of number of victims during that period.
- Countries that are victims of Black Basta. Source -
Characteristics
Motivation
Black Basta proved to be a major threat to industrial sectors. Approximately 30% of its targets pertained to sectors such as manufacturing, engineering, and construction. This preference is due to these sectors' high reliance on operational continuity, their ability to make meaningful payments, potentially outdated IT infrastructures that are less focused on cybersecurity, as well as the high valuation of their data on the black market. According to sources, Black Basta has managed to obtain payments close to $100 millions, mainly in the United States and Germany. While the group's targets were companies of all kinds, most of the registered victims belonged to medium-sized organizations.
Infection and spread
Black Basta employed phishing techniques to infiltrate the networks of its targets, taking advantage of methods that evade detection by antivirus solutions, such as sending emails that prompt victims to download a ZIP file containing an ISO image, a strategy designed to circumvent security mechanisms, as ISO files are not commonly blocked or marked as dangerous by security systems. safety. The infection process uses different methods and vulnerabilities to carry it out:
- Initial access with Qakbot (CVE-2022-30190): in the typical scenario observed on Windows systems, the ISO image contains a malicious DLL infected with Qakbot, a well-known Trojan, also identified as Qbot or Pinkslipbot. Some IOC samples revealed a 'hijacking' of the Windows calculator (calc.exe) process. This method could allow attackers to execute malicious code on the victim's system with a veneer of legitimacy, reducing the chances of detection. Once the victim installs it on the system, the malware is capable of performing different malicious actions, such as monitoring, logging keystrokes, harvesting login credentials, and spreading to other systems on the network using lateral movement techniques. Once inside the system, it uses misleading names within the root drive such as “C:\Dell” o “C:\Intel” to deploy some of the malicious arsenal.
- Privilege escalation (CVE-2020-1472, CVE-2021-42287 and CVE-2021-34527): network scanning is carried out using tools such as SoftPerfect, netscan.exe, and WMI services, to identify and disable different security products. Once Black Basta infects a system, it initiates its propagation phase, performing a detailed analysis of the network by using commands such as 'net view', 'arp', 'ipconfig' or 'netstat' to map potential additional targets. It then uses credential extraction tools such as Mimikatz to acquire NTLM passwords and hashes, allowing it to perform privilege escalation.
Operation
During its operation, it maintains active communication with a command-and-control (C&C) server to move laterally through the network and manage infections.
After the ransomware is executed and before the file encryption process is generated, a ransom note is created in a readme.txt file on each affected computer with a custom id. Included in the note is a TOR address with ransom instructions.
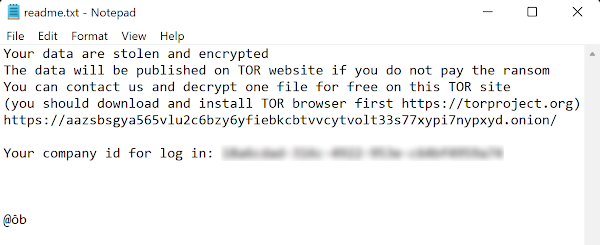
- Black Basta ransom note example. Source -
Among other peculiarities, the ransomware also writes a Random-letters.jpg file inside the %TEMP% directory that it will use to change the victim's desktop background, displaying a message about the encryption procedure by the Black Basta group, as well as where the ransom instructions can be found.
Evasion of detection and recovery
Black Basta employs a number of advanced techniques to evade detection by security solutions and to hinder file recovery from backups:
- Obfuscation and polymorphism: It uses techniques to alter its digital signature and code structure, making it difficult for signature-based antivirus solutions to detect it.
- Living Off the Land (LotL): Uses legitimate system tools and processes (such as PowerShell, WMI, and PSExec) to execute malicious actions, complicating the differentiation between legitimate and malicious behaviors by security systems.
- Anti-analysis and sandbox detection: incorporates detection routines of analysis and sandbox environments, stopping their execution or altering their behavior in the presence of analysis tools, by verifying user interaction or the presence of certain software artifacts.
- Memory execution (Fileless): Executes part of its payload directly in memory, minimizing its footprint on the file system and avoiding detection by tools that monitor the hard drive.
- Disabling security solutions: Attempts to disable security tools present on the system, such as antivirus and firewalls, by forcibly terminating their processes or modifying security rules to prevent them from working.
- Deleting backups: Using commands such as vssadmin delete shadows /all /quiet, wmic shadowcopy delete, and bcdedit /set {default} bootstatuspolicy ignoreallfailures, the ransomware is capable of identifying, deleting, or encrypting files from backups, preventing their recovery without the decryption key.
Encryption
Black Basta encrypts victim data using a combination of ChaCha20 and RSA-4096. The encryption key is generated using the C++ function rand_s, resulting in a random hexadecimal output. Before starting the whole process, it will boot the system in safe mode and then start encrypting all the files on the device.
To speed up the process and improve its efficiency, the ransomware encrypts the first 64-byte fragments, leaving 128 bytes of data unencrypted. Once finished, the file changes its extension to '.basta', automatically modifying the file's icon.
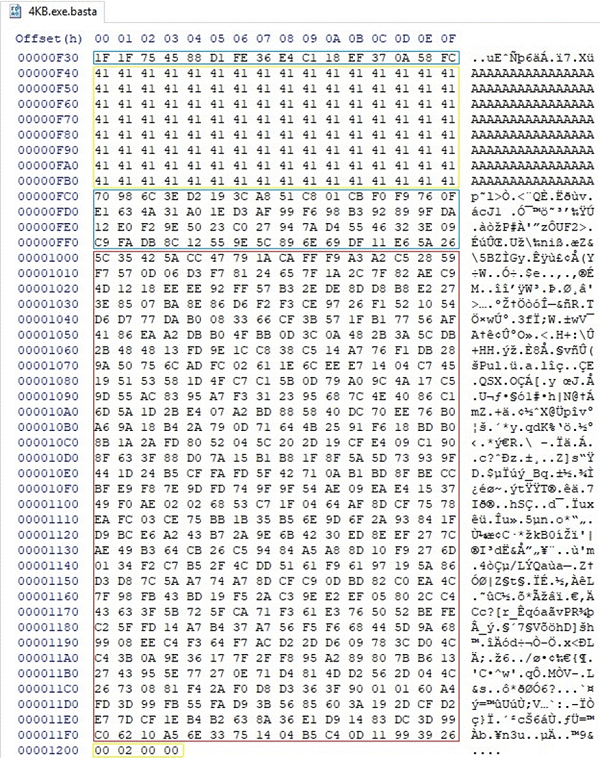
- File Encrypted Using Black Basta. Source -
Response & Disinfection
Recently, the discovery of a significant vulnerability in the encryption mechanism employed by the Black Basta ransomware was disclosed, focusing on a flawed implementation of the ChaCha algorithm, specifically in the management of the key flow for the XOR operation on 64-byte segments of the targeted data.
SRLabs experts identified that the key flow advance was not executed properly, causing the reuse of the same 64-byte segment for XOR encryption of all data blocks, instead of using unique segments for each block as would be expected.
Through a detailed analysis of this anomaly, the experts managed to isolate the 64-byte key applied in this procedure, allowing them to develop the ‘Black Basta Buster’ decryption tool, which consists of several Python scripts. Some of the most relevant are:
- Decryptauto.py: Attempts to automatically determine zero-block encryption and applies it to the entire file.
- Decryptblocks.py: Decrypts a file by applying XOR to a key in known locations within the file.
- Extractblock.py: Extracts a 64-byte fragment from a file, potentially used as an encryption key. It can be useful to take that block as a decryption key.
- Findblocks.py: Search for small fragments in large files.
- Ranges.py: Identifies the positions and lengths of encrypted bytes in a file.
- Readcounter.py: Read the footer of an encrypted file to determine the extent of the encryption.
- Vmlsfs.py: Useful for running virt-ls on decrypted virtual machine files to assess file system integrity.
- Xorblocks.py: Applies the XOR operation to a single fragment of a file at a specific offset..
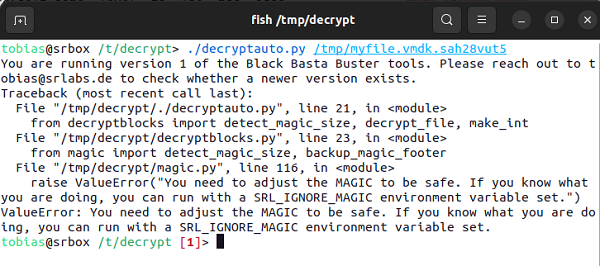
- Example of a decryptauto.py script used on an encrypted file. Source -
However, file recovery is subject to different situations or conditions:
- The tool only works with the versions of files encrypted before the end of 2023, as the authors of the ransomware appear to have resolved this vulnerability.
- On the other hand, files smaller than 5 KB are unrecoverable, while those up to 1 GB can be fully restored. In the case of larger files, partial recovery is possible.
Conclusions
The Black Basta ransomware study has enabled the current cybersecurity landscape to gain greater visibility into the current dynamics of cyber threats, especially those based on ransomware, offering several key lessons:
- Increased adaptability and sophistication of threats: Black Basta is a perfect example of the ongoing trend towards the development of more advanced ransomware threats, using complex evasion techniques and robust encryption algorithms. At the same time, this trend highlights the need for the evolution of defense systems in terms of dynamism and sophistication.
- Cybersecurity collaboration: The possibility of decrypting files affected by Black Basta, thanks to the discovery of vulnerabilities in its algorithm, underscores the importance of thorough research and deep technical knowledge of ransomware. Much of the success of this research work lies in the collaboration and sharing of knowledge within the cybersecurity community, demonstrating the ability to adapt and counter new and evolving threats.
- Importance of cybersecurity awareness: As the actors behind these threats continue to refine their methods, cybersecurity training continues to remain an essential pillar for both businesses and end-users. Being prepared with up-to-date knowledge of ransomware tactics, defense tools, and incident response strategies is key to effective protection against ransomware-type threats like Black Basta.









