CAPEC in the ICS world

Before starting to talk about CAPEC (Common Attack Pattern Enumeration and Classification), it is necessary to understand what attack patterns are. These patterns are different qualities or characteristics that differentiate some cyberattacks from others, such as, for example, that an attacker can access the device because the victim has entered a malicious URL that has been sent to you in an email, or that, when downloading a file, the file is infected and downloads a specific virus, etc. All these patterns are known thanks to the investment made in the investigation of cyber-attacks since, in order to know these patterns, a lot of time and data are needed to ensure that the attack patterns are correct, and the error is minimal.
To obtain this information, there are currently many technologies, one of which is the honeypot, a technology that simulates a process or activity of the company so that the attacker carries out attacks on this simulation and not on the one in production. This makes it possible to investigate all the attacks that the honeypot has suffered in order to find attack patterns and improve the cybersecurity of the machine being simulated.
Another way to obtain new attack patterns is to monitor the communications and activities performed by the devices to save all the necessary information after suffering a cyberattack.
CAPEC was established by the U.S. Department of Homeland Security as part of the SwA (Software Assurance) which was a CS&C initiative, initially conducted in 2007 but, over the years, has been improved with the help of multiple participations and contributions to become a mechanism to identify, collect, improve and share cyber-attack patterns with the cybersecurity community. Therefore, CAPEC is a catalog where the most common cyber-attacks can be reflected in order to help the community understand them and implement new measures that can prevent cyber-attacks.
Operation of CAPEC
On the official MITRE website: CAPEC - Common Attack Pattern Enumeration and Classification (CAPEC™), it is possible to find multiple options, the CAPEC list being one of the most interesting. In this list you will find the different attack mechanisms, sorted by the following categories:
- Attack mechanisms. Source -
These categories are very generic since they are made up of different subcategories called meta-attack patterns which, in turn, are made up of different cyberattack patterns of different types, such as detailed patterns or standard patterns. The following image will help to understand a little of what has been explained above.
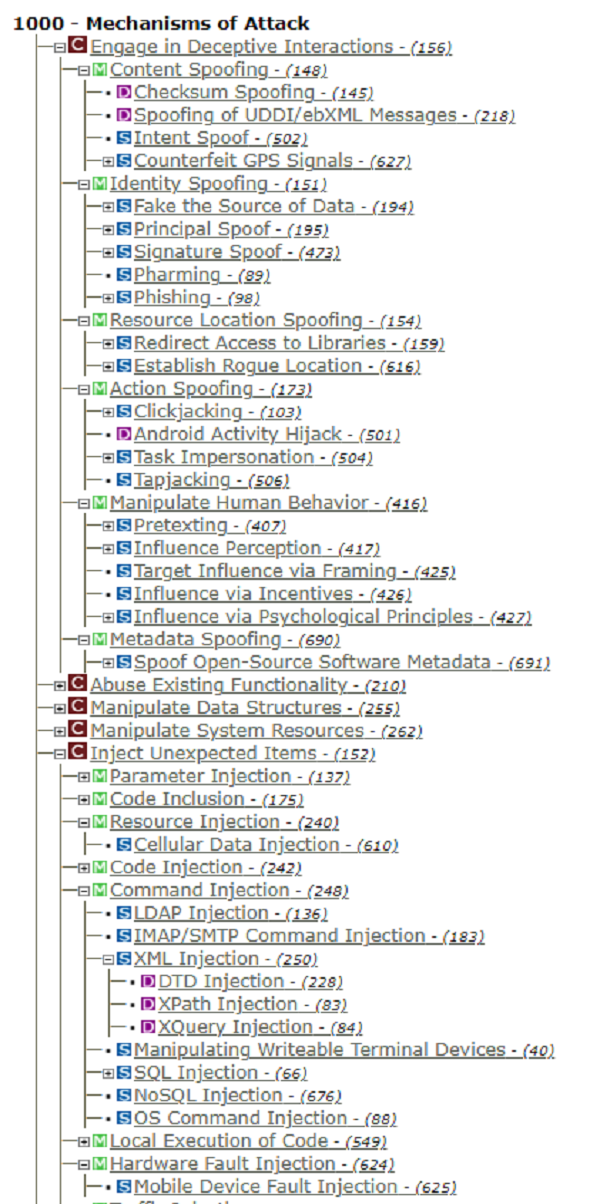
- Categories of attack mechanisms. Source -
By clicking on a specific pattern, a new page will appear with a specific description of that pattern, other patterns that are related to that pattern, the consequences that may occur after suffering this attack and its relationship with the MITRE ATT&CK taxonomy, as shown in the following image..
- Example CAPEC. Source -
CAPEC in the industrial control systems
Due to the new CAPEC updates and the continuous cyber-attacks suffered by the industrial sector, a list has been made where you can see all the patterns that have been detected that are related to the industrial world. The following image shows all the detected patterns related to the industrial sector.
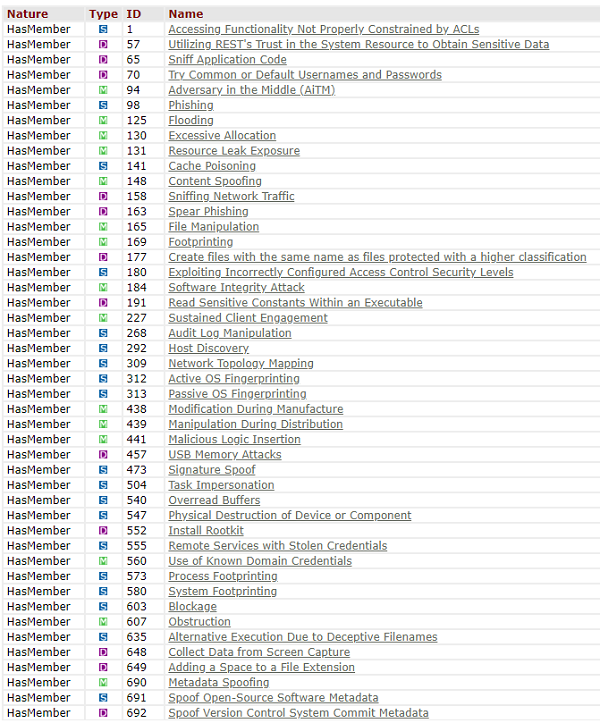
- SCI patterns. Source -
Conclusion
On the one hand, thanks to this type of initiatives, the cybersecurity sector is growing considerably as they help to have a certain level of intelligence that allows to anticipate a cyberattack or to know how to eliminate or mitigate it when it happens.
On the other hand, this type of activity brings together specialists in the sector who try to share their knowledge so that cybersecurity becomes increasingly more mature.
Finally, the fact that this type of initiative is starting to be introduced in industrial cybersecurity is a great step forward since the industrial sector is one of the sectors where maturity in cybersecurity is quite low and the damages that can occur are very high, both for society and for companies. This low level of maturity is due to the fact that until recently the devices were connected locally and access to these devices could only be done in a physical way, so cybersecurity was not so critical, however, today, this has changed.









