Cybersecurity applied to railway technology

The railway industry has accompanied everyone from the first industrial revolution to the current digital era. Now, this new paradigm involves the integration of advanced technologies in all areas, including railways, with the aim of improving efficiency, safety and the interconnectivity of people and systems.
However, all these transformations also entail a significant increase in cybersecurity risk. In this article, it will be explored, from a cybersecurity perspective, the operation of railway systems, the challenges they entail at the device cybersecurity level and how the regulations that apply to the railway sector have been evolving.
Technologies used in the railway sector
The railway sector, like road transport, is governed by a standardized signaling system, currently defined by ERTMS (European Rail Traffic Management System).
According to traditional signaling, there are a series of systems in charge of protecting trains, all of which are governed by a series of basic principles to be complied with:
- Avoid collisions or collisions between trains.
- Authorize the circulation of trains according to their itinerary and safety.
- To prevent derailments due to high speed.
- A range of driving modes can be selected according to need.
These principles are implemented through a series of elements (light signals, signage, track change rail systems…) that allow train drivers to obtain information on how the track is located and follow a specific route at any given time. In addition to these traditional elements, there are also protection systems, called ATP or Automatic Train Protection, whose objective is to control the behavior of the train in unexpected situations, among other secondary functions.
Given the wide variety of existing ATPs, the ERTMS system was adopted in the European area with the aim of ensuring railway interoperability between member countries.
This system has three levels, each of which is divided according to the necessary capacities and requirements. In addition, this system is composed of three key technologies:
- Beacons: are devices that emit electromagnetic signals that are picked up by the train's receiver, obtaining information necessary for the driver. This type of device is mandatory from level 1 onwards.
- GSM-R: based on GSM connectivity or Global System for Mobile Communications, is a digital communication system used to transmit voice and data services through radio frequencies. In the railway sector, this type of devices have cryptographic keys that allow the authentication and encryption of communications. Also, the use of specific frequencies for the sector is used. This system is only applicable in levels 2 and 3 of the ERTMS system.
- RBC: radio bloc center, this system enables the sharing of specific geographic data, track data and the cryptographic keys of the trains in circulation. The use of this technology depends on the ERTMS level used; the use of this system is applicable to ERTMS levels 2 and 3.
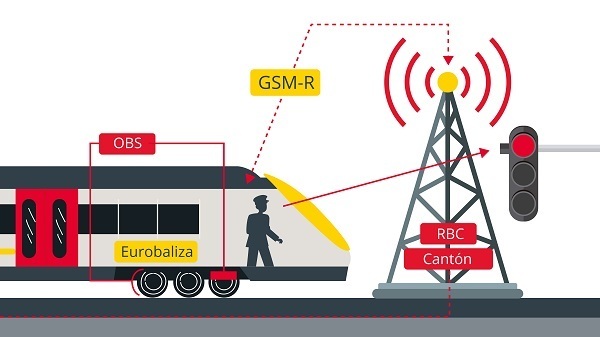
- ERTMS systems. Source. -
In conjunction with ATPs, in the railway sector, as in other industrial fields, industrial control systems (ICS) are used to control, in real time, the operation of railway equipment. These systems, like an industrial plant, have the typical PLC and RTU located in different stations and physical locations, but their integration is done in a special way, through devices called UOC (Unified Control Center). These devices allow the integration of different industrial protocols used in the sector (OPC-UA, Modbus TCP, BACnet, IEC 61850, MQTT...), providing more contextualized information used, for example, for integration in SCADA systems.
Cyber-attacks on the railway sector
The rail industry is no exception to the current trend of increasing number and complexity of cybersecurity incidents. Over the past few years, these attacks have had multiple consequences: from travel delays to data theft and reputational damage for companies in the sector.
For all the above reasons, the railway sector is a highly complex sector with respect to its communications and therefore a sector with a high exposure to cyber-attacks. Another factor that is compromised is the so-called IT/OT convergence, since there are areas in which IT information is shared with certain specific OT information.
An example of these IT/OT convergence zones would be the cyber-attack on Iranian railway sector systems that occurred in July 2021, following the attack on railway IT systems using the MeteorExpress malware. This attack led to the shutdown of several websites of the Iranian national railway system and disrupted train service. The cyber-attack caused information screens to show that scheduled trips had been delayed or cancelled.
The operation of this malware consisted in the use of a wiper, responsible for deleting local files from the computers, causing the screens used for its configuration to become unusable.
During the evolution of this cyberattack, the attackers used a series of processes to achieve their goals within the system. First the malware disconnected the affected devices from the network. Then it added a series of exclusions in Windows Defender allowing the execution of batch files. After that, the malware performed obfuscation tasks, such as deleting Windows event logs, preventing information about its activity from being saved. Finally, they started the Meteor wiper, the MBR (Master Boot Record) partition blocker, which is responsible for providing the information needed to turn on the computer, and the computer screen blocker.
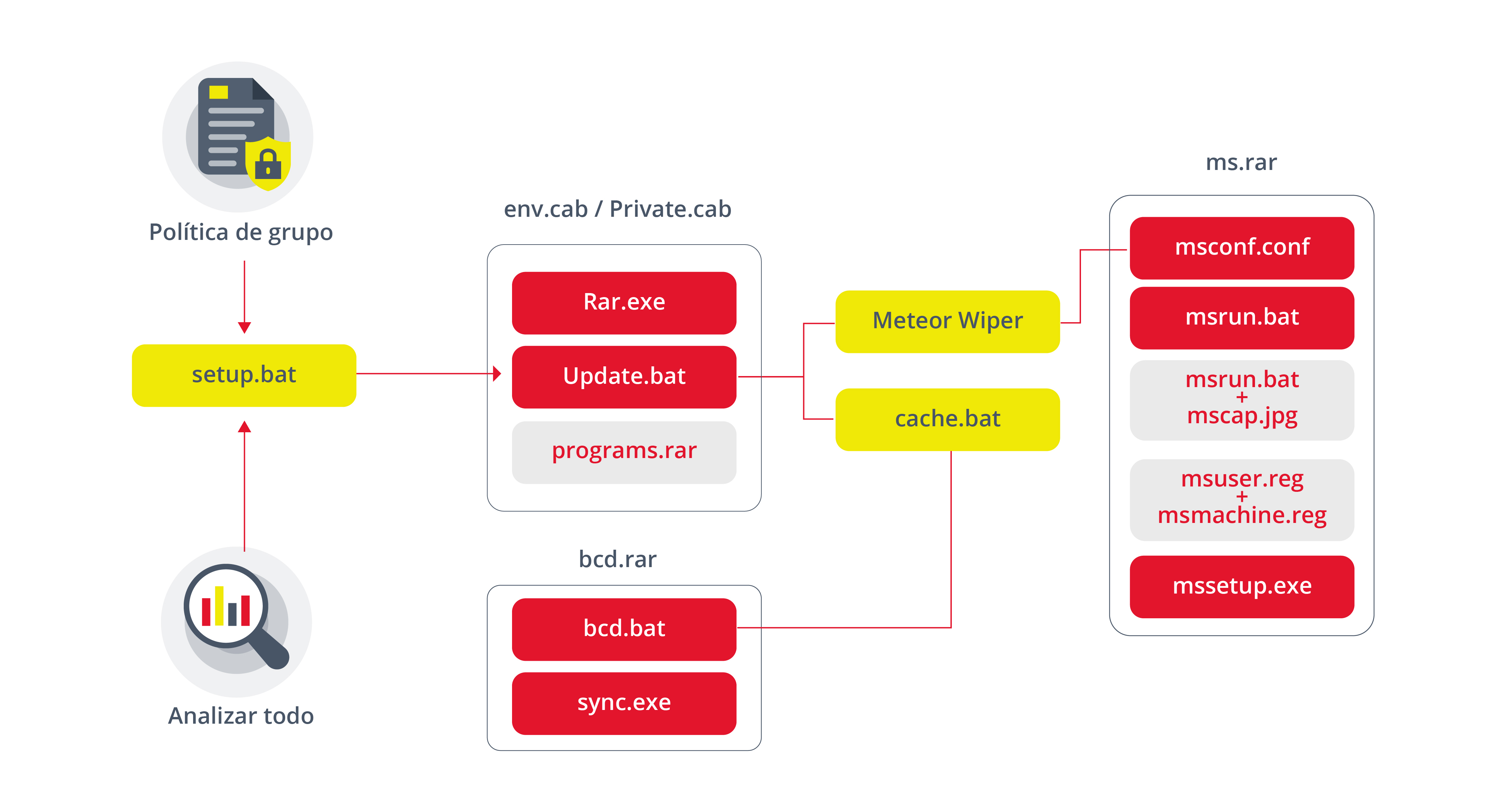
-Diagram of the malware used in recent attacks against the railway system. Source. -
More recently, in August of the same year, another example of a cyber-attack in the railway sector was experienced in Poland. This cyber-attack caused more than 20 trains to be stationary for hours, causing delays in the transport of goods and people.
Despite being a cyber-attack of considerable impact, it is not a very complex cyber-attack. According to the investigations carried out, radio signals were used to shut down the railway system, triggering the emergency stop of the safety systems, designed to stop the system securely in case of emergency. Since there were no authentication measures or traffic encryption, the stop signals were interpreted as authentic by the system, making it easier for the attackers.
Cybersecurity trends
In recent years, with the digitalization of the economy and services, new cybersecurity challenges have arisen for organizations adopting the latest technologies in the market. Specifically, it could be considered that the development of cybersecurity in the railway environment is one of the most difficult challenges in the current scenario due to the complexity, criticality and extension of the sector.
Faced with this challenge, ENISA (European Union Agency for Cybersecurity) has published a series of documents in recent years recommending a series of guidelines and recommendations for the railway sector:
- ENISA Transport Threat Landscape: oriented to identify the main threats and sources of potential incidents in the transportation sector, allowing to obtain a clearer picture of the possible cyber-attacks applicable to the sector and what are their motivations.
- Zoning and Conduits Railways: which describes good network segmentation and connectivity practices for the railway sector. Similar to IEC 62443, used in most industrial sectors, it defines a methodology of independent network segments (zones) connected by communication bridges (ducts) protected by traffic control elements.
In parallel to these standards, the 4SECURail program was created, which seeks to create a series of tools, allowing the generation of collaborative processes and tools designed to coordinate a joint response of all European railroads in the event of a cybersecurity incident.
In parallel to these standards, the 4SECURail program was created, which seeks to create a series of tools, allowing the generation of collaborative processes and tools designed to coordinate a joint response of all European railroads in the event of a cybersecurity incident.
Conclusion
The difficulty of implementing cybersecurity in the railway sector presents a unique complexity as it is incredibly heterogeneous: it groups a complex geographical distribution, an infinite variety of technologies (new and traditional), multiple types of cargoes with different requirements for their transportation, changing national and international legislations and requires the collaboration of public and private, national and international organizations in every part of the sector; and last but not least, it demands a high level of security in order to guarantee the safety and privacy of users and workers who interact with it every day.
However, applicable regulations are currently being implemented, such as ENISA, the PIC law, NIST 2 and IEC 62443, which provide a series of guidelines and recommendations to be followed to prevent future incidents. All this, together with the correct adoption of new security technologies, are going to be key tools to increase the maturity of rail sector infrastructures and face the constant evolution of cyber threats.
In short, although the railway sector represents a challenge in terms of cybersecurity, it also represents a great opportunity for improvement with respect to the traditional methodology, due to its position as a strategic international sector, as well as its exemplary position as a point of intersectoral and international collaboration.









