Dragonfly 2.0 mapping on MITRE ATT&CK ICS Matrix

Currently, industrial infrastructures or ICS (industrial control systems) are one of the main targets of attacks by cybercriminal groups. In many cases, this poses a serious threat not only to the production of the affected organization or company, but also to the health of workers, the population or even the country in which the company is located, if it is classified as a critical infrastructure or if its business is highly relevant to the state.
Throughout this article, a malware with a relative impact in the industrial world will be analysed, allowing to know how this type of attacks are carried out and how it should be analysed.
Attack description
The attack selected for this analysis is Dragonfly 2.0, which, although not as well-known as other types of attacks, was relevant because of the method and objectives behind it.
This attack was orchestrated by the Dragonfly group, well known for carrying out different attacks on companies in the energy sector. It emerged in 2011 and in 2014 they executed one of their best-known attacks, successfully attacking different industrial control systems in the energy sector in Central Europe.
The Dragonfly 2.0 attack was executed on December 11, 2017, by inserting a USB into a critical infrastructure engineering station in the Middle East.
As will be seen below, the Dragonfly group is motivated by sabotage as well as learning about the infrastructures it attacks, and Dragonfly 2.0 in particular employed tactics and techniques from MITRE ATT&CK's ICS Matrix to achieve its goal.
Locations attacked
Dragonfly 2.0 was not executed against a single target, but was deployed worldwide, affecting countries such as the US, Turkey and Switzerland, as shown in the following illustration:
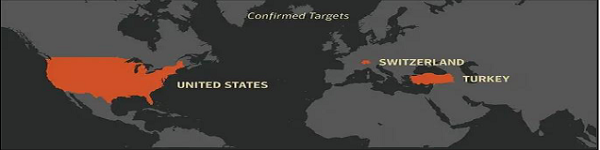
- Countries affected by Dragonfly 2.0. Source -
Vectors of infection
To obtain an initial analysis, not only of the attack but also of the group, it is advisable to investigate the access methods or infection vectors used by the group of cyber attackers.
Dragonfly 2.0 stands out not only for its relative impact in different industrial environments, but also for its versatility in using different infection vectors to gain access to the network, among the most prominent:
- Phishing by email: first infection vector used by Dragonfly in different attacks on industrial infrastructures. This type of infection vector in the case of the Dragonfly group is characterised by the sending of malware via phishing emails to personnel related to the target company's industrial environments.
- Watering hole attacks: This term refers to how Dragonfly directed its attacks through websites trusted by industrial plant operators. This type of infection vector requires a very advanced study of the target company. Moreover, in the specific case of Dragonfly, it is characterised by the implementation of exploit kits on the websites so that the malware could be directed to the industrial operator's server.
- Legitimate software compromised: Dragonfly compromised different pieces of legitimate software in order to transfer the malware to the targeted devices.
- Trojans: Since 2017, they have also implemented the use of the Shelter evasion framework, with capabilities to develop applications with Trojans to gain control or remote access to target machines.
Tools used
Dragonfly 2.0 employed different types of well-defined tools that are very common in generic attacks on industrial environments:
- Phishing: the analysed (targeted) attack used phishing campaigns by attaching malware to emails.
- Trojans: Trojan software was used as an initial weapon to gain access to the network of a computer used by a user with operator permissions in the industrial plant. Among the Trojans used were traces of Backdoor.Goodor, Backdoor.Dorshel and Trojan.Karagany.
- Phishery Kit: use of the Phishery toolkit to carry out e-mailing attacks to steal credentials.
- RAT: remote access Trojan, introduced into the target system, via phishing, to gain remote access.
Tactics and techniques used
As will be seen in this section, Dragonfly 2.0 used up to nine of the twelve tactics available in the MITRE ATT&CK ICS Matrix. On the other hand, it used up to seven techniques, with their corresponding sub-techniques, during the execution of the attack. These tactics and techniques are described in our article on matrix design.
First, the tactics used and why they are used are listed along with the techniques used grouped within the tactics:
- Initial Access: Several of the tools listed above indicate the use of this tactic to try to gain access to the system:
- Driven-by Compromise: use of websites to gain access to victims' systems.
- Exploitation of Remote Services: exploiting vulnerabilities in the software to introduce specially designed software that allowed remote actions to be executed.
- Remote Services: used the SMB protocol to remotely obtain, compress and encrypt files.
- Spearphising Attachment: use was made of the Backdoor.Oldrea RAT distributed via Trojanised installers attached to emails sent to victims.
- Execution: Dragonfly 2.0 executed commands on control systems.
- Commnad-Line Interface: CLI (Command Line Interfaces) was used to interact with the systems, so that domain user accounts could be listed and newly created accounts could be added to the administrator group.
- Valid Acoyuntes: Dragonfly 2.0 was mainly characterised by information theft, it is not fully proven, but, there is evidence of credentials theft to be able to execute other steps of the attack as without those credentials it would be of great complexity.
- Privilege Escalation: the execution of the malware allowed actions to establish accounts with administrator privileges.
- Exploitation for Privilege Escalation: accounts with maximum privilege level were added after obtaining domain user accounts.
- Evasion: the use of different applications to mask the malware clearly indicates the use of this tactic.
- Masquerading: Dragonfly 2.0 was characterised by masking the malware to avoid suspicion on the part of operators.
- Discovery: SMB was used to try to obtain different information.
- Remote System Discovery: the association of this tactic with the Dragonfly 2.0 attack is determined by the use of Backdoor.Oldrea. This type of malware plugin makes it possible to discover all servers within the Windows network that the attacker can access via the network.
- Remote System Information Discovery: this technique made it possible to remotely obtain information from remote systems and peripherals also via Backdoor.Oldrea.
- Lateral Movement: by downloading software and using remote services, Dragonfly 2.0 executed lateral movements to gain higher privileges.
- The techniques used within the Lateral Movement tactic are the Exploitation of Remote Services, remote Services and Valid Accounts explained in previous tactics.
- Collection: the use of the Backdoor.Oldrea Trojan indicates the possibility of using different techniques gathered in this tactic, and although there is no verified information, it is strongly believed that Dragonfly 2.0 sought to collect information about the target.
- Theft of Operation Information: used to steal information from the production environment.
- Impact: the theft of information from industrial control systems.
- Tactics and techniques used. -
Conclusion
Throughout the article, an introduction to the Dragonfly cybercriminal group has been given, which provides basic knowledge about the group, its methods and its targets. Subsequently, the different attack vectors used by the group have been introduced in order to, together with the basic knowledge explained, understand the basic functioning of the attacking group, and this methodology can be extrapolated to any other cyberattack group.
On the other hand, the tactics and techniques employed during the Dragonfly 2.0 attack have been defined and explained, with a rationale as to why these tactics and techniques were employed, allowing for an advanced understanding of the attack and the ability to apply mitigation measures to reduce the potential for damage in the event of a similar attack.
As explained throughout the articles dedicated to the Top 20 mitigations for industrial environments, part 1 and part 2, there are different possibilities to mitigate attacks using tactics and techniques described in the MITRE ATT&CK ICS Matrix, therefore, the combination of an advanced knowledge of the attacking group and the tactics and techniques used together with the possible mitigations, make an organisation or industrial company better able to defend itself against a similar attack.









