DrDoS cyberattacks based on the Memcached protocol
After the preliminary study denial of service (DoS) cyberattacks alongside any of their variants set out in the article “DrDoS: characteristics and operation,“ this new article is going to address how the Memcached protocol is used as a tool to develop a DrDoS variant of a DoS cyberattack.
Memcached
As regards data storage systems and objects in the cache memory, Memcached is widely used by website servers that handle information from databases, since it is freely licensed and has versions for all Windows, Linux and macOS operating systems. The purpose of this service is that the responses to web requests, which reach the server, be made faster; to achieve that, the requested data must be stored in a RAM memory, instead of requiring to be accessible through external resources.
Just like other cache systems, Memcached is based on hash tables kept in the RAM of computers in which, as they reach their storage limit or when their validity time has elapsed, their stored data is deleted, leaving space available for new ones from the most recent requests. The customers do not access a specific server, but rather communicate with servers over port 11211, by default, using library functions, and they have set up a list of possible servers to which they can connect to search the data.
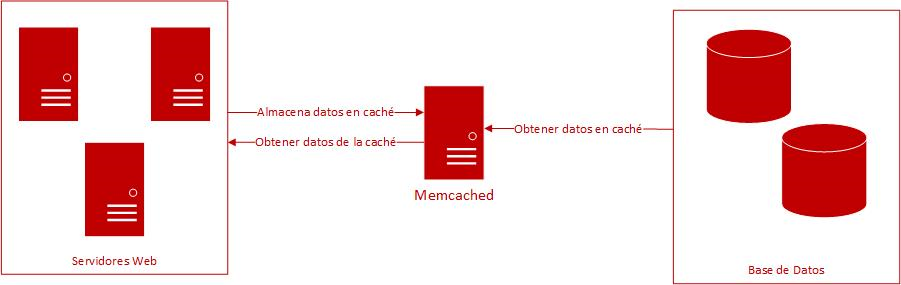
- Figure 1. Diagram of operation of Memcached. -
This type of system is used by well-known websites, such as YouTube, Facebook, Twitter, Reddit and GitHub, among others, and even Google offers a Memcached service, which is implemented using the functions of its own API.
Attack vector
The starting point must be that DrDoS attacks based on the Memcached vulnerability use the misconfigured servers of this system that execute versions earlier than 1.5.6.
As a first step, the attacker identifies the vulnerable servers, which are accessible by UDP, and generates a large number of modified requests, which it sends en masse over those localised servers through a botnet it controls to flood the victim machine with responses.
In those requests to the server, the attacker falsifies the IP address (IP spoofing) by changing its IP to that of the victim machine so that the Memcached servers respond unintentionally, concentrating the response packets on the target system. Moreover, to ensure denial-of-service requests are modified at source so that the Memcached intermediate servers compose responses with more data and generate large-size packets. Thus, the size of the response packet received by the attacked computer may be 51,000 times larger than the source request packet.
This is all possible thanks to the UDP protocol for the end-to-end connections, since it does not require a confirmation or acknowledgement upon establishing the initial connection or sending a large volume of data, as does happen TCP.
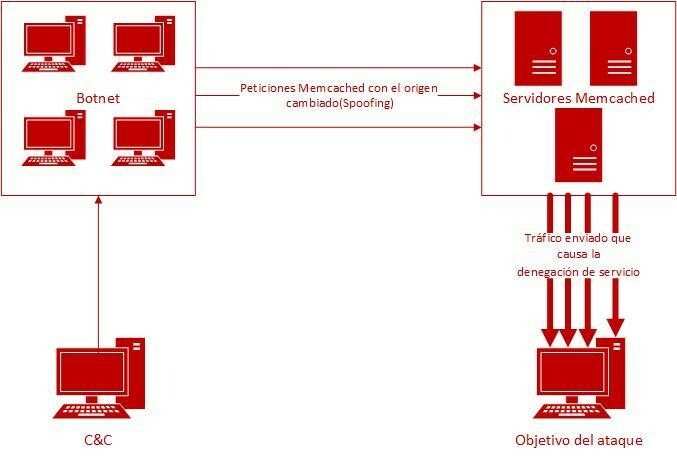
- Figure 2. Diagram of the attack on Memcached. -
As a result of the attack, and depending upon the scale of the victim’s resources, the victim will not be capable of absorbing and processing all the traffic and data arriving from intermediate servers, causing the system or services for legitimate users to be unavailable due to the errors that occur when loading the requested data.
Moreover, the consequences can also affect intermediate servers, leaving them inoperative by saturating their resources due to their having to service and process the bulk requests they receive from the botnet.
Prevention
The following command may be used from the administration console to find out whether a Memcached server is vulnerable:
nmap -p 11211 --script memcached-info [IP Address]
If the response is blank, the server is not vulnerable. Otherwise, it will be vulnerable.
On the other hand, to prevent an own Memcached service from being used as a tool to carry out a DoS attack against third parties, the following preventative measures are recommended:
- Updating Memcached software. It is necessary to verify that the servers using this technology, whatever their operating system may be, are updated to the most recent version, or at least that the installed version is at least 5.6., since from that version on the vulnerability is corrected, disabling the possibility of default UDP connection.
- Disable UDP. If it has not been possible to upgrade to a secure version, it is recommended that the UDP port be disabled if it is not used. To do so, the settings file where the service is hosted (the location of this file will depend upon the platform and software being used) must be modified. The changes to be applied will depend upon the operating system on which Memcached is running.
- Filters for the UDP/TCP port. If none of the foregoing options can be applied, it is recommended that filters be established through the firewall for the port where the server operates, which by default is 11211.
- Limiting the traffic on Memcached servers. It is possible to limit the speed of the IPv4 and IPv6 traffic and the length of the packets exchanged between the source and destination Memcached ports by configuring additional filters in port 11211, through the firewall.
- Reduce the exposure of Memcached servers on the Internet. This would be possible by filtering the IP addresses that may access the server. Memcached services are intended to be used in trusted
Detection and evidence
Intense and abnormal activity related to UDP traffic on port 11211 would indicate that our Memcached system is being a victim of an amplified denial-of-service attack, either as the target of the attacker or as an intermediate reflection system.
To check whether the data packets are the same or show obvious signs of tampering, it is necessary to review the network traffic, checking the source addresses of the requests received, and thus confirm the attack.
In early, the tools used to monitor the “status” of the machine (the programs that monitor the use of resources, such as processes, memory and disks) can detect abnormal events related to Memcached. Another great help are the alerts that can be generated by the SIEM systems deployed or the alerts generated by the set of filters set out in the firewall.
Response and recommendations
If the evidence confirms that there has been a DrDoS attack on Memcached, it is necessary to act quickly, applying the operation and event management protocol for this type of attack as defined above. This procedure must include the following:
- Invalidating the server cache used to amplify the attack. The following command allows you to clear the cache on servers that are being used to carry out a traffic amplification, which will invalidate the attack:
flush-all
- Identifying the attack’s source IP address and the destination IP address, along with the destination port: compiling all the useful information to communicate to the Internet Service Provider (ISP), in order that it can be blocked.
- Contacting the ISP or hosting provider: reporting the incident and conveying the necessary information so that the necessary traffic filtering measures may be applied, so that attacks can be prevented.
- Blocking and filtering unwanted traffic. Data compiled in advance can be used to configure filtering rules on firewalls and routers to prevent requests reaching your own Memcached server.
- Obtaining technical assistance: contacting the IT technical services suppliers contracted for this purpose or the leading public computer emergency response teams (CERT) such as INCIBE-CERT.
Once the attack is finished and the service has been restored to normal, it is necessary to analyse the causes, identify the possible vulnerabilities that made it possible, and take measures to eliminate the system’s weaknesses or, at least, improve prevention, and thus avoid it recurring.









