Fuxnet: the malware that paralyzed ICS systems

In recent years, the industrial sector has faced a growing threat of cyberattacks. These attacks go beyond simple digital intrusions, as they have the potential to block the supply of basic services such as electricity and water, and completely paralyze a company’s operations. Even a brief interruption can have devastating consequences, highlighting the urgent need to strengthen cybersecurity in the industrial domain.
It is important to highlight that carrying out these cyberattacks has become increasingly difficult. Many of these infrastructures are not directly connected to the internet, which is known as “security through obscurity”, or have external connections that are very wall secured and controlled.
In recent days, the hacker group Blackjack publicly disclosed information about the cyberattack they conducted using the Fuxnet malware against the company Moscollector. This company, based in Moscow, specializes in the construction and monitoring of underground networks, water infrastructures, sewage and communications. Fuxnet represents an evolution of the well-known Stuxnet malware.
Based on the information provided by Backjack, it is deduced that the malware was likely deployed remotely. Once deployed, its objectives were as follows:
- Device Lockdown: This was achieved by closing remote access, services such as ssh, http, telnet, and SNMP. This made impossible to stop the attack remotely.
- Destruction of important files and directories. Attackers deleted servers, workstations, and databases, resulting in the deletion of 30 TB of data. Additionally, they removed the routing table to render their ability to communicate with other devices inoperative. They also managed to obtain sensitive information from the databases.
- Dumped database information. Source. -
- Destroying NAND memories. NAND flash memory is used in a variety of devices, including computers and mobile phones. Unlike other of storage, NAND memory does not require continuous power to retain data, making it highly popular for its ease of reprogramming and low cost per terabyte of storage. However, it has a significant drawback in that it has a limited number of write cycles. Fuxnet exploits this vulnerability by repeatedly rewriting the NAND memory until it deteriorates completely, rendering the chip unusable.
- Destroying UBI volume. This is done to prevent the sensor from restarting. It involves rewriting the UBI volume. Normally, this volume waits for a specific number of bytes to be passed to it, but the malware passed fewer bytes than expected, causing the device to indefinitely wait for completion.
- Denial of monitoring service. Monitoring data is recorded by sensors connected to the gateway via the RS485/Meter-Bus channel. Fuxnet writes random data repeatedly on the Meter-Bus channel, preventing sensors and the gateway from sending and receiving data.
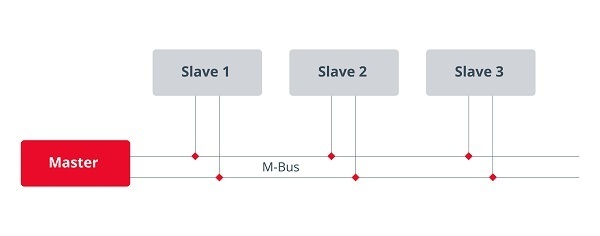
- Meter-Bus operation diagram. Source. -
Blackjack claims to have compromised 87.000 devices, but based on the previous point, it is assumed they infected only the sensor gateways and attempted further damage by flooding the Met-Bus channel connecting various sensors to the gateway. This resulted in the gateway devices being rendered unusable rather than the final sensors themselves.
The scope of the attack was extensive, affecting sensors and compromising sensor gateways, routers, management software (SBKManager software package), and the sensor monitoring system.
An attack on essential services can cause a wide range of damages, from disruptions in service delivery to emergency situations posing life-threatening risks to people. For instance, in hospitals, a cyberattack can paralyze critical systems such as patient management, electronic health records, or network-connected medical equipment, potentially delaying or preventing access to necessary medical care. In airports, an attack could interfere with air traffic control systems, lead to flight cancellations, and even jeopardize the safety of passengers and crew. In summary, the consequences of an attack on essential services can be highly significant, with serious implications for the physical security, health, and overall societal well-being of individuals.
To prevent these types of attacks, several countermeasures can be implemented, including:
- Network segmentation (MITRE ATT&CK ICS Mitigations M0930): dividing the network into smaller segments and restricting access between them can limit the spread of malware in case of an intrusion.
- Firewalls and packet filtering (MITRE ATT&CK ICS Mitigations M0937): configuring firewalls to control and filter incoming and outgoing network traffic can help block malicious activities.
- Strong authentication (MITRE ATT&CK ICS Mitigations M0804 and M0932): implementing robust authentication measures, such as strong passwords and multi-factor authentication, can prevent attackers from accessing systems and devices unauthorizedly.
- Network monitoring: using network monitoring tools to detect suspicious activity and anomalous behaviors can help quickly identify and mitigate potential attacks.

-Network monitoring. Source. -
- Personal training and awareness: training staff in cybersecurity practices and raising awareness about risks associated with phishing, social engineering, and other attack tactics can reduce the likelihood of successful attacks targeting the human factor.
- Incident response: developing and practicing incident response plans can help minimize downtime and mitigate the impact in case of a successful attack.
By implementing these countermeasures, along with a defense-in-depth strategy, organizations can strengthen their security posture and significantly reduce the risk of falling victim to attacks like the one mentioned.
Conclusion
The case of the Fuxnet malware highlights the sophistication and devastating potential of cyberattacks targeting critical infrastructure. This article has underscored the importance of understanding the tactics and objectives of such threats, as well as the urgent need to strengthen cybersecurity in the industrial sector. With knowledge gained from studying past cyber incidents and implementing preventive and proactive measures, organizations can enhance their ability to detect, contain, and mitigate the impacts of future similar attacks.









