SASE architecture in your cybersecurity strategy

Traditional cybersecurity paradigms have become outdated with the advent of the cloud. According to IBM's 2023 'Cost of a Data Breach Report', 45% of security breaches are related to cloud services, and 80% of organizations surveyed suffered a cloud security-related incident in the last year.
As the number of users connecting from various locations and accessing highly sensitive data stored in the cloud increases, it is essential that we stop to think about how to strengthen our cybersecurity strategies to meet the new challenges. Even the legislation has had to be updated, as is the case with the last update of the National Security Scheme, in 2022, where an operational framework (op.nub) linked to the protection of cloud services has been incorporated. In summary, systems providing cloud services to the public sector must adhere to specific security measures based on the type of cloud service (SaaS, PaaS, or IaaS), covering aspects such as: pentesting, transparency, encryption and key management, and data jurisdiction. Third-party services must be certified under a recognized methodology and if they offer a security service, they must meet additional requirements.
In this context, SASE (Secure Access Service Edge) systems can help with compliance with this and other adaptations of the law and regulations. These systems emerge as a paradigm shift in traditional architectural principles, moving away from the traditional centralized model to a decentralized cloud delivery model.
SASE is characterized by the convergence of comprehensive network capabilities with network-related security capabilities, including NG Firewall, Secure Web Gateway, CASB, and ZTNA. This convergence makes it possible to provide a more secure and flexible model of connections, directing traffic intelligently, in addition to performing a more advanced security inspection directly focused on the cloud.
Advantages of SASE
Having a SASE offers numerous advantages to today's organizations. Some of its most outstanding advantages are:
- Platform flexibility: SASE architecture is characterized by being platform-agnostic, giving the security infrastructure maximum flexibility. This allows businesses to adapt and expand their security infrastructure in a scalable way as they grow.
- Hardened security: SASE services are based on the principle of Zero Trust and enforce an organization's zero trust policy. Users can only access the organization's applications if they have a legitimate need, which strengthens security and reduces the attack surface. This is complemented by solutions, such as CASB, NGFW or (FWaaS), anti-APT, DLP, WAAP or Remote Browser Isolation (RBI) browsing sandboxing, which protect against security threats.
- Centralized policy management: Another benefit is that it unifies the management of consistent security policies across the organization and simplifies compliance and security management across the organization. As a consequence, you can see a reduction in the operating costs of the business.
- Performance improvements: Unifying management avoids having to 'jump' from one system to another, with the associated latency penalty accruing per system. As a result, users who connect to cloud SaaS applications and latency-sensitive applications such as collaboration suites, video, VoIP, and web conferencing experience a significant improvement in quality of experience (QoE), which is reflected in increased performance.
Operation and applications of SASE solutions
SASE builds a secure, software-defined, wide-area network (SD-WAN) for the management of the organization's network traffic, thus supporting traditional inspection and verification methods, such as traffic routing through MPLS (Multiprotocol Label Switching) switching services, enabling a smooth transition to a more modern and secure network architecture.
This means that organizations can continue to use their existing MPLS connections, while adopting the SD-WAN and security capabilities provided by SASE.
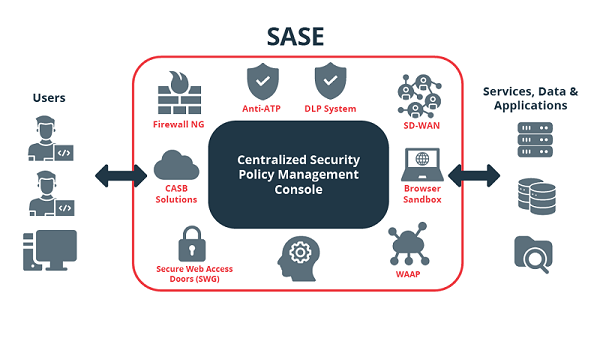
- Basic diagram of how SASE works. -
SASE systems deploy a number of components that benefit security professionals, IT administrators, and other roles within the organization. Let us take a closer look at some of its practical applications:
- Centralized security policy management console. It allows you to define and manage security policies through a centralized interface, from which to control all components, simplifying security policy management and helping to ensure regulatory compliance.
- CASB (Cloud Access Security Broker) solutions. They provide visibility and control over data and cloud services, improving data protection and helping to comply with privacy regulations.
- SD-WAN (Software-Defined Wide Area Network). It facilitates the management and operation of wide-area networks, enabling secure connectivity for remote employees and optimizing network performance.
- Next-generation firewalls (NGFWs). It provides additional features such as application filtering and intrusion prevention, enhancing real-time traffic inspection and filtering to detect and mitigate cyber threats.
- Advanced Threat Prevention System (ATP). It detects and responds to advanced threats and anomalous behavior on the network, providing early detection and response to advanced threats.
- Data Loss Prevention System (DLP). They protect against the loss or leakage of sensitive data, ensuring the protection of corporate data and helping to ensure compliance with regulations.
- Secure Web Access Doors (SWG). They provide protection against online threats and control of applications and data on the web, ensuring safe browsing and improving the security of data and applications in cloud environments.
- Web Application and API Protection (WAAP). It improves the security of web applications and APIs by detecting and mitigating vulnerabilities and targeted attacks, providing an additional layer of protection when interacting with web services.
- Browser Sandbox (RBI). It provides an isolated environment for browsing the web, protecting corporate systems against malware and other online threats, by running potentially dangerous web content in a separate environment.
Challenges
Despite their many advantages, incorporating SASE systems into the business environment comes with certain challenges and challenges. Transitioning to SASE is not an overnight process, as modifying the enterprise security architecture requires significant investment and a maturation process. However, the most effective strategy is usually a gradual adaptation, establishing a well-defined roadmap that guides each step of the way.
The key to a successful transition to SASE is to avoid the temptation to implement everything at once. The divide-and-conquer strategy is usually quite effective. It is preferable to start by implementing a section of the system, and not necessarily the most critical, but the one where the company perceives that there is a lower risk. This approach allows the organization to gain understanding and experience with the new security architecture, facilitating a smoother and more structured implementation of the rest of the SASE components over time.
A possible implementation strategy for SASE could start with securing the enterprise perimeter, securing remote access with ZTNA, and diverting external traffic to the centralized firewall, to progressively migrate on-premises applications to the cloud, with a unified policy configuration and native to the cloud.
Regardless of the strategy proposed by the organization, the goal is to gradually converge towards a new, more secure ICT architecture, mitigating risks and optimizing investment.
Conclusion
The usefulness of SASE lies in its ability to ensure data protection in the cloud, facilitate secure connectivity for remote employees, and provide real-time traffic filtering. In addition, they simplify the management of security policies, optimize network performance, and ensure regulatory compliance under a zero-trust approach.
The need to adapt to a SASE security architecture is reflected in the increase and complexity of today's cyber threats, such as malware in general or ransomware and data theft in particular. The repercussions of not having these security measures in place can be devastating, ranging from the loss of crucial data to the disruption of business operations, not to mention the reputational damage that can be suffered by the organization. The adoption of these security measures is no longer seen simply as an initiative-taking action, but as an essential investment to protect and strengthen the resilience of organizations in an ever-evolving digital world.
Implementing SASE gradually aligns the organization with a more sustainable and structured approach, allowing a progressive adaptation to the new security architecture. In addition, a step-by-step approach also provides the time needed to educate and prepare staff, adapt existing policies, and make necessary adjustments to the IT infrastructure to ensure a successful transition to a secure architecture.









