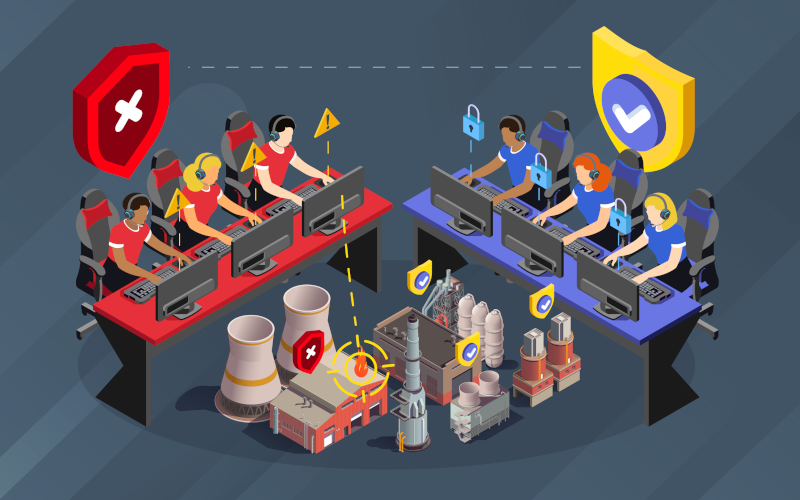
MITRE Caldera OT stands out mainly for being an open-source tool that allows the simulation of different cyber-attacks in industrial environments. This tool was created by MITRE and CISA (US Cybersecurity and Infrastructures Security Agency), as the experts saw the need to be able to improve and understand cybersecurity in industrial environments without using a high number of resources.
In addition, this tool is designed to be used by both the Red Team and the Blue Team, allowing both teams to collaborate with each other to improve the level of cyber security in these environments.
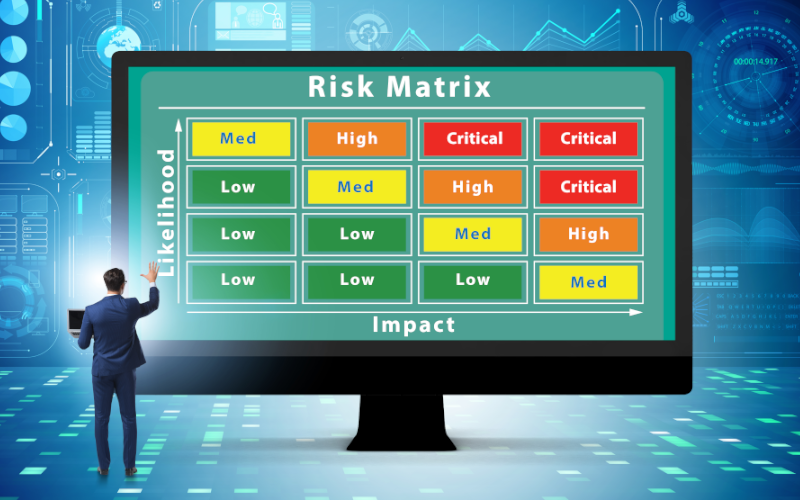
In the era of interconnection and digitization, industrial control systems (ICS) are increasingly exposed to cyber threats. These systems are vital for energy production, manufacturing and critical infrastructure management, and their protection has become an essential priority.
Risk analysis is fundamental in this context, as it allows identifying, assessing and prioritizing the risks that can affect ICS. This process, ranges from technical vulnerabilities to emerging threats, and is crucial for developing effective mitigation and protection strategies.
In this article, the challenges and solutions related to risk analysis in ICS will be explored, as well as the importance of the IEC 62443-3-2 standard in this critical process.
This post presents some lines of action that should be followed to deal with a DrDoS cyberattack based on the PortMapper protocol, describing in detail the prevention, identification and response phases to follow.

This post presents some lines of action that should be followed to deal with a DrDoS cyberattack based on the LDAP protocol, describing in detail the prevention, identification and response phases to follow.

This post presents some lines of action that should be followed to deal with a DrDoS cyberattack based on the QOTD protocol, describing in detail the prevention, identification and response phases to follow.

This post presents some lines of action that should be followed to deal with a DrDoS cyberattack based on the SSDP protocol, describing in detail the prevention, identification and response phases to follow.

En este post se presentan algunas líneas de actuación que deben seguirse para hacer frente a un ciberataque DrDoS basado en el protocolo CharGEN, describiendo detalladamente las fases de prevención, identificación y respuesta a adoptar.

The automotive world has always been one of the most cutting-edge sectors in terms of the technology used, which is why today's cars are equipped with technologies such as Bluetooth, NFC, GPS, etc., which improve different aspects such as comfort, fuel efficiency and increased safety.
But these implemented technologies can also bring with them serious problems, such as the risk of cyber-attacks that can affect passengers in the vehicle, both at the level of personal data and physical security.
For this reason, this article aims to provide an insight into some of the cyber-attacks that smart cars have suffered and how cyber-security is evolving and adapting to make more and more vehicles cyber-safe.

The evolution of communications in society is also having an impact on the industrial world. With the arrival of 5G, many industrial companies have considered migrating some of their communications to take advantage of the characteristics of this new mobile communications band, such as the reduction of latency times, the increase in connection speed or the exponential increase in the number of devices that can be connected to the network. These characteristics fit perfectly with the industrial mentality, where there are a multitude of interconnected devices between which there cannot be a communication cut due to the criticality of the processes they implement.
This article aims to comment, in addition to all the advantages that 5G provides to the industry, the different uses that can be given currently and the complexity of implementing these communications in some devices for subsequent deployment in the industry. Also, to specify possible vulnerabilities in communications using 5G networks.

This post presents some lines of action that should be followed to deal with a DrDoS cyberattack based on the ARD protocol, describing in detail the prevention, identification and response phases to follow.



