Secure web gateway (SWG)

In today's cybersecurity context, where threats are becoming increasingly sophisticated and attack profiles more diversified, organizations are faced with the challenge of protecting an increasingly dispersed and decentralized IT infrastructure. This scenario demands a rethinking of security strategies, leading to the adoption of models such as Zero Trust , a philosophy that operates under the principle of "never trust, always verify", rather than assuming that everything within the corporate network is secure. In the cloud environment, users and resources can be anywhere, which means a significant transformation in the way identity and access to resources are managed.
Las tecnologías SASE (Secure Access Service Edge) play a critical role in supporting the implementation of Zero Trust in cloud environments. It combines network and security capabilities into a single, integrated solution, making it easy to transition to an identity- and context-based security model, rather than relying solely on the network perimeter. SASE seeks to simplify security and network management, offering secure access to enterprise resources, regardless of user or resource location.
Within the SASE ecosystem, the Secure Web Gateway (SWG) plays a critical role. Unlike other SASE components such as CASB, which are specifically designed to manage security in cloud-based applications and services, SWGs focus on monitoring and controlling web traffic, filtering web content, and providing protection against threats.
So, what sets it apart from a traditional gateway? An SWG brings a broader focus and more advanced capabilities. While a traditional gateway focuses primarily on inspecting and controlling network traffic at the corporate network perimeter, an SWG also implements browsing usage policies, prevents access to malicious websites, and offers protection against advanced threats such as phishing and malware. Additionally, an SWG is best suited for cloud environments and for businesses with a mobile or remote workforce, as it is not limited to the physical perimeter of the network and can apply security policies consistently, regardless of the user's location..
SWG Architecture
The architecture of the SWG is composed of a series of characteristic elements:
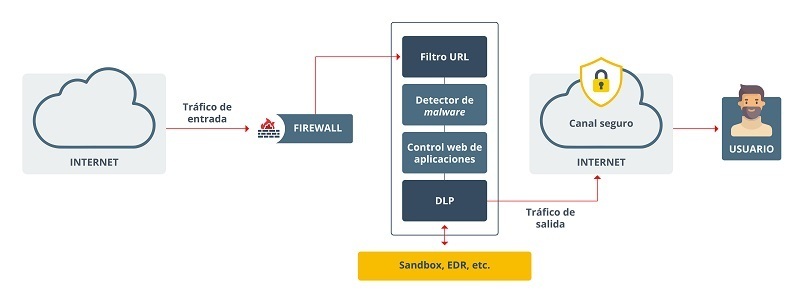
- Rendering filtering inbound web traffic using a cloud SWG. -
- URL filtering: in addition to blocking websites based on blacklists and categories, URL filtering also blocks inappropriate content using specific URL patterns, keywords, and content categories. This ensures a professional online environment that is in line with company policies. For example, if an employee tries to access an inappropriate website during business hours, URL filtering can automatically block this request based on the company's Internet usage policies.
- Detection and filtering of malicious code using malware analysis that combines signature-based detection (to identify known malware) and heuristic techniques (to detect unknown variants). For example, if a user downloads a malicious file, it would be possible to identify and isolate the file before it causes damage. SWGs also analyze network traffic to detect compromised devices that could be part of botnets. In addition, they help mitigate DDoS attacks by blocking malicious traffic.
- Popular Web Application Controls: uses deep packet inspection and pattern recognition technologies to monitor and control web application usage. For example, a company can configure the SWG to allow the use of telematics communication software, only for voice calls, blocking the rest of the file transfer functions to prevent leakage of sensitive data.ses deep packet inspection and pattern recognition technologies to monitor and control web application usage. For example, a company can configure the SWG to allow the use of telematics communication software, only for voice calls, blocking the rest of the file transfer functions to prevent leakage of sensitive data.
- Data Leak Prevention (DLP): implements complex algorithms and rules to identify sensitive information flowing through the network. For example, if an employee tries to send an email with a document that contains sensitive customer information, the DLP module can detect this pattern, block the email from being sent, and alert security administrators.
- Integration with components: SWGs often integrate with other security services, such as sandboxes, intrusion prevention systems (IPS), and detection and response systems (EDRs), for more comprehensive protection. Also, with secure reverse proxy. This component acts as an intermediary between users in your organization and the websites or applications they are trying to access. Reverse proxy is useful for inspecting encrypted traffic.
The implementation of an SWG can vary depending on the service model:
- On-Site mode (Local): in on-site deployment, the SWG is installed and operated within the company's physical infrastructure, using proprietary hardware and servers. This approach offers maximum control over security and configuration, as well as lower latency, as traffic does not need to leave the internal network to be inspected. However, it requires an investment in hardware, and trained personnel for its maintenance and updating. It is ideal for organizations that require a high level of customization and control, and that have the ability to manage their own IT infrastructure.
- As IaaS (Infrastructure as a Service): deploying a SWG as IaaS means using a cloud provider's infrastructure to host the SWG, while maintaining control over its configuration and management. It allows for customization and control but requires considerable technical knowledge to manage and maintain the underlying infrastructure. It's suitable for businesses that are looking for a more customizable solution than SaaS but don't want to or can't invest in on-site hardware and maintenance.
- As PaaS (Platform as a Service): an SWG deployed in a PaaS model provides both the necessary hardware and software. It offers a balance between control and convenience, allowing some customization and control over the configuration, without the responsibility of managing the underlying infrastructure. It's ideal for organizations looking for a greater degree of control than SaaS offered, but with less complexity than a full IaaS or on-site implementation.
- As SaaS (Software as a Service): as SaaS, the SWG is completely managed by a third-party vendor. This option eliminates the need to worry about infrastructure, maintenance, or upgrades, as the provider takes care of everything. It's the preferred choice for businesses that want simplicity and don't have the resources or inclination to manage the security infrastructure themselves, but the service's configuration options will be limited.
Best Practices for Implementation
The SWG solutions available on the market vary widely in terms of features, capabilities, and deployment models. Some of these solutions are offered by third parties as managed services or software products, while others are open source, allowing for greater customization and adaptability to specific needs. In addition, organizations have the option to build their own SWG solution in a modular way, from individual components, allowing for more precise adaptation to the company's infrastructure and security requirements, although it may require more effort in terms of integration and maintenance.
However, in the process of implementing a SWG, regardless of whether you opt for a third-party, open-source, or custom-built solution, there are critical steps that will need to be considered: it is crucial to conduct a detailed risk assessment and define specific technical needs, such as identifying potential threats and assessing existing infrastructure. This includes assessing existing workflows and determining the technical and human requirements for operating the SWG. Choosing a suitable SWG solution depends on multiple factors such as the size of the organization, the nature of its operations, compliance requirements, and existing infrastructure. In addition, the decision must balance the need for security with considerations of cost, ease of use, and maintenance. Therefore, careful evaluation and detailed planning are essential to ensure that the chosen SWG solution is effective and sustainable in the long term.
In addition, in case the solution does not incorporate it, systems must be established for continuous monitoring and analysis is essential to detect suspicious events and evaluate the performance and effectiveness of the SWG. Finally, keeping the SWG up-to-date is crucial to protect against new threats. This includes applying security patches and signature updates in a timely manner.
Conclusion
The adoption of SWG as part of security strategies such as Zero Trust and SASE is a critical step for organizations looking to protect their resources in an increasingly decentralized, cloud-based IT landscape. Not only do SWGs help protect an organization's business data and network, but they also allow users to access the web securely and productively.
Properly choosing and implementing these solutions requires a careful assessment of risks, technical needs, and detailed planning to ensure that the chosen solution is effective and sustainable in the long term. Keeping the SWG up-to-date and continuously monitoring it are essential practices to ensure effective protection against emerging threats. Finally, it is critical that users are informed and trained on security policies and the proper use of Internet resources, as an SWG is only as effective as the users who use it.









