Behavior analysis as a cybersecurity tool
The vast majority of organizations, regardless of their size or sector, usually work with ICT systems to carry out their activity. These systems handle information about how users, systems, processes, and events interact within your infrastructure and with your resources.
All of this data could be collected and analyzed to provide crucial findings about user behavior, usage patterns, and operational trends. However, as these organizations grow and their operations become more complex, the number of records generated periodically can increase exponentially, becoming unmanageable. Fortunately, within this ocean of information, patterns of behavior are hidden that can indicate possible threats, both external and internal, whether intentional or not.
The analysis of user and entity behavior, UEBA (User and Event Behavioral Analytics), emerges as a fundamental technology, since it uses machine learning, and machine learning algorithms to monitor, analyze and protect the organization against internal, potentially harmful activities.
Having UEBA-type tools gives the organization a deep insight into the behavior of users and entities and helps to better understand its digital ecosystem, identify possible risks, and respond quickly and effectively when abnormal behaviors are detected, and with it, possible threats to the security of the organization.
Operation and benefits
UEBA systems analyze user behavior and entities using different elements as parameters, including: user location, timestamps, indicators of compromise, system rules, user device type, roles, permissions, file access, application usage, or access frequency. All this to identify abnormal behaviors, based on established patterns and behaviors.
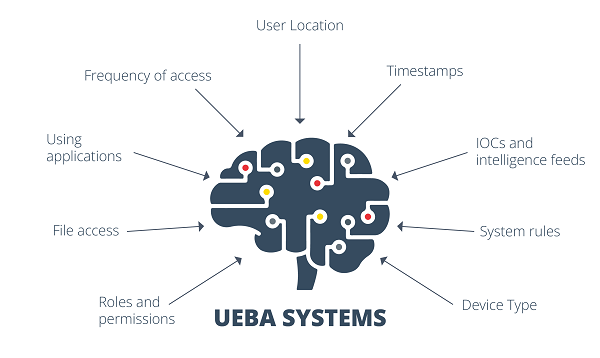
- Elements that feed the intelligence of UEBA systems. -
In general, they offer a series of benefits that strengthen the cybersecurity strategy of organizations. Its ability to:
- Detection of anomalous behavior: thanks to advanced algorithms, it builds behavioral profiles based on historical patterns and security policies, which helps distinguish between legitimate and suspicious activities, offering valuable findings about irregularities. For example, if an employee accesses information they wouldn't normally access or downloads large amounts of data, the system will detect this and alert the security team. In addition, machine learning techniques allow tools to learn and adapt to new patterns and emerging tactics.
- Reduction of false positives: it is a complementary tool to existing security solutions, which improves the overall detection capabilities of the organization, by integrating with other security systems, minimizing unfounded alarms.
- Improved threat responsiveness: Operating in real time, these tools constantly analyze data flow and user interactions, identifying patterns of unusual behavior almost instantly. This early detection not only prompts immediate interventions, but also gives organizations a critical window of opportunity to take preventive or corrective action before threats escalate.
- Improved operational efficiency: Using processes and machine learning, security professionals have more time to focus on real attacks.
Use of UEBA in accordance with the protection of personal data
As we have seen, UEBA solutions are powerful tools in cybersecurity, but their configuration and operation must be done in accordance with the legislation on the protection of personal data.
The General Data Protection Regulation (GDPR) establishes a series of fundamental principles that any data processing must follow:
- Data minimization: These solutions, by their nature, tend to collect a vast amount of information for the purpose of detecting anomalous behavior or suspicious activity. However, it is imperative that these solutions are restricted to collecting only the data essential to meet their goal, avoiding unnecessary storage of personal information that might not be relevant to their function.
- Transparency: Organizations must not only ensure that data is collected and processed in a transparent manner, but also inform individuals about the nature and purpose of this processing. This includes clarifying how and why behavioral profiles are being built and what security measures are being taken to protect that information.
- Location of data: If a provider is located outside the European Economic Area (EEA), organizations must ensure that international data transfers comply with the provisions of the GDPR. This means that adequate safeguards, such as standard contractual clauses or adequacy decisions, must be in place to protect the transferred data.
Technology and tools: the case of OpenUBA
UEBA tools can be very useful for a wide range of professionals within an organization, from system administrators and security analysts to data scientists who leverage these platforms to develop and fine-tune models that improve the detection of anomalous behavior.
There are a wide variety of options available, including open-source solutions that provide organizations with a flexible and scalable alternative to their security needs.
An example of them is OpenUBA, a tool that has a growing community of users that supports and enriches its development. It features a lightweight architecture and compatible with any SIEM, benefiting from technologies such as Spark and ELK to process data efficiently and on a large scale. In addition, it includes a library of models fed both by the community and internally.
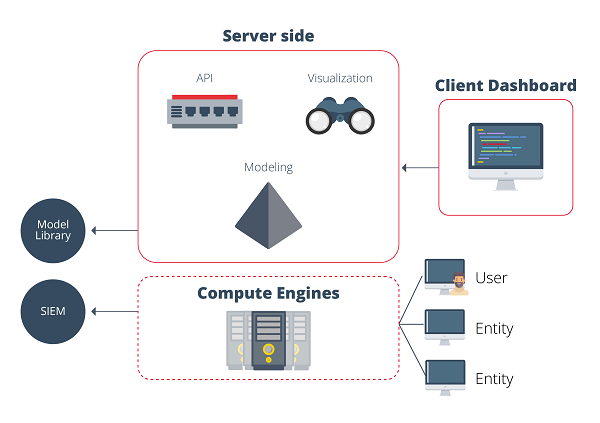
- OpenUBA architecture. Source.-
OpenUBA's threat model is based on the MITRE ATT&CK framework, enabling organizations to have a deeper, more contextual understanding of the threats they face.
Conclusion
Ensuring the protection of information is an intrinsic responsibility for all organizations. UEBA solutions, which focus on analyzing user and entity behavior, have emerged as one of the leading tools in modern security strategy, helping to identify anomalous patterns and potential security compromises.
The importance of UEBA analysis lies in its ability to provide a detailed view of user behavior, allowing organizations to quickly detect potential internal or external threats. This early detection capability is essential in preventing security breaches and protecting critical assets. However, with the power of these tools comes significant data protection responsibility. These solutions collect and analyze large volumes of user behavior data, which can pose privacy challenges.
It is crucial that organizations implementing this technology do so with an ethical approach, ensuring that users' privacy and digital rights are not compromised. Therefore, it is important to consider not only the effectiveness of the solution in terms of threat detection, but also its compatibility with personal data protection regulations.









