Exploring M-Bus, security and efficiency in telemetry communications

Currently the M-Bus or Meter Bus protocol is one of the most widely used in both the industrial and residential sectors, since its main function is to read the data generated by the meters, regardless of whether they are for water, gas, electricity, heating, etc. One of the main features of this protocol is that it uses a hierarchical master/slave communication system, allowing to collect the data generated by the sensors through the requests created by the master, in addition this type of communication can use different types allowing a much more flexible and scalable network architecture. The problem is the way in which communications are sent since being master/slave it has to go between devices passing the information between all devices.
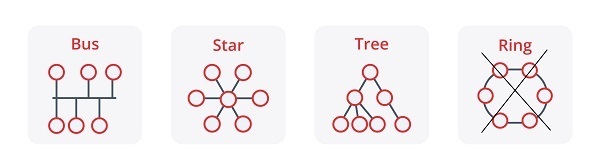
- Typologies allowed in M-Bus -
Another of the most outstanding characteristics of this protocol is the voltage required for its correct operation, which usually ranges between 36 and 42 VDC, which makes it necessary to install voltage boosters since the connections commonly used do not generate such high voltages.
Other important features of the M-Bus protocol are:
- There is a wide range of products on the market due to their European standard.
- The networks have the capacity to extend up to 5 km in length.
- Each network can manage up to 5,000 end devices each.
- M-Bus protocol has a simple connection (a 2-wire polarity cable) that does not require shielding.
On the other hand, one of the major problems of this protocol is its low level of cybersecurity, since the developers of this protocol focused more on the effectiveness of communications and on ensuring that they were carried out in the shortest possible time. This can be seen in the fact that the data sent is in plain text, which means that an attacker with access to the communications, either through a connection to the network or to the device, can acquire valuable information and use it for malicious purposes.
In addition, due to new technological advances and the high use of this protocol, a wireless version called WM-Bus or Wireless Meter Bus has been created, which allows devices in remote areas to communicate with each other, thus reducing the cost of installation that would be involved if they were wired.
Alternative WM-Bus
The WM-Bus alternative allows the reading of the devices wirelessly being this an ideal solution for the creation of industrial wireless sensor networks or IWSN (Industrial Wireless Sensor Networks) giving the ability to place sensors or actuators in hard to reach places to control them remotely. This is not the only advantage brought by this evolution of the protocol, since it is more robust than its predecessor and also provides better power efficiency and increases security in the protocol.
The basic characteristics of this alternative are as follows:
- Support for unidirectional or bidirectional communication.
- It works at different frequencies:
- 169 MHz.
- 433 MHz.
- 868 MHz.
- Support for AES-128 encryption and authentication.
- Availability for alarms and malfunctions.
- Star topology with the option of introducing repeaters.
- Long battery life, between 15 and 20 years.
- Maximum range varies depending on the frequency at which it works:
- 500 meters a 868MHz.
- 2000 meters a 169 MHz.
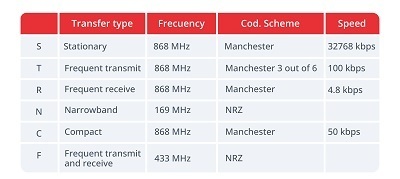
- Transfer modes. Source -
The security features introduced in the protocol are as follows:
- Confidentiality:
- AES-128 type encryption and authentication is allowed, providing enhanced privacy, which means that no one can get into the communication if it is not desired.
- Integrity:
- Ensures that the message received is the same as the message written by the sender.
- Authentication:
- Ensures that the message received comes from the original device.
- Protection against 'playback':
- This makes it impossible for the receiver of the message to record or save it and resend it later.
Vulnerabilities discovered on M-BUS
The most known vulnerabilities addressed are those affecting the PiiGAB M-Bus SoftwarePack 900S (PiiGAB M-Bus). Here 9 vulnerabilities of different criticality were discovered, which are:
- CVE-2023-36859.
- Vulnerability rated high with a score of "8", whereby PiiGAB M-Bus does not validate received ID strings before processing them, which could result in code being sent to it and executed by it.
- CVE-2023-33868.
- CVE-2023-31277.
- CVE-2023-35987.
- Vulnerability classified as critical with a score of "9.8", whereby PiiGAB M-Bus makes use of credentials entered the code to perform authentication
- CVE-2023-35765.
- CVE-2023-32652.
- Vulnerability rated high with a score of "8.8", whereby PiiGAB M-Bus SoftwarePack 900S does not properly sanitize user input, which could allow arbitrary commands to be injected when entering usernames.
- CVE-2023-34995.
- CVE-2023-34433.
- CVE-2023-35120.
Solutions o mitigations for risks
Due to the cybersecurity problems that the M-Bus protocol has, different methods have been sought to increase its level of cybersecurity. The most relevant methods are the following:
- Update the devices to the latest possible version, allowing you to avoid possible bugs or failures in the software.
- Introduce devices such as firewalls that allow you to create rules to limit or block unwanted communications.
- Introduce technologies to be able to visualize and control the communications made with this protocol, the best examples are IDS (Intrusion Detection Systems) and IPS (Intrusion Prevention Systems).
- External access to devices should be done through cybersecure protocols and in a controlled manner.
In addition to these solutions, you can implement others that will also increase the cybersecurity of communications, for this it is advisable to read the article Top 20 Mitigations in Industrial Environments, part 1 and part 2, where you will find a greater number of mitigations and explained in a more detailed and complete way.
Conclusion
As we have seen throughout this article, the M-Bus protocol is one of the most widely used protocols in devices whose main function is to send data in real time. These devices are widely used in many sectors such as water supply, electricity, heating, etc.
The big problem of this protocol is the low level of cybersecurity because when developing this protocol was thought more in the functionality, this low level of cybersecurity can be detected because the data is sent in plain text and have been able to find different vulnerabilities.
Over time, different solutions have been developed, such as the creation of the WM-Bus protocol or the implementation of firewalls or other technologies to secure communications.









