
Currently, there is a constant evolution in the technologies and implementations made in Industrial Control Systems. On one hand, some of the most common implementations for the improvement of industrial systems infrastructures are digitalization and the use of cloud technology. On the other hand, the increase in communication protocols and IIoT devices (due to the growth of the Industry 4.0) generates a large volume of traffic that is difficult to control and secure.
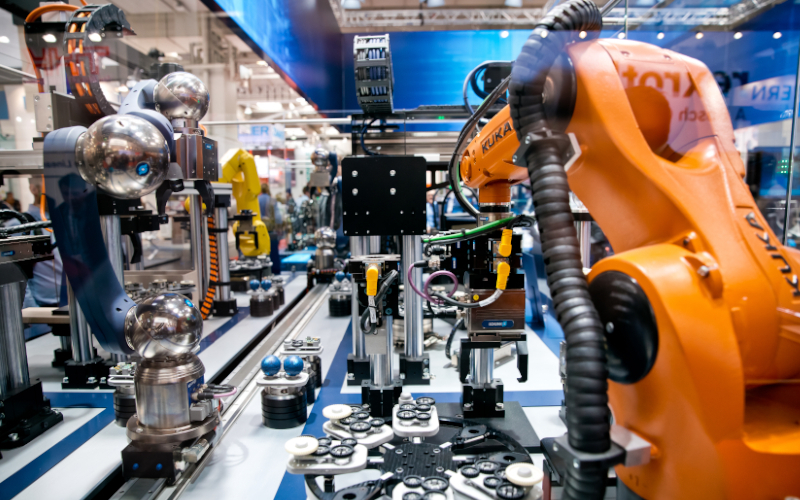
Within the industrial world, there are some sectors such as robotics, which has evolver considerably. This has led to the need to update all the regulations and standards, both in terms of physical (safety) and cybersecurity. (security). Given that the robotics sector is and will increasingly become a highly technical sector with exponential growth, the need to update all documentation has been promoted by a large group of companies in the sector, which, above all, have focused their concerns on the cybersecurity of the industrial robotics world.

En este estudio, se expone brevemente el origen y evolución de la amenaza ransomware LockBit 3.0, a través del análisis de varias muestras maliciosa, con el objetivo de facilitar la información necesaria para poder identificar las características propias de este malware, su comportamiento y técnicas empleadas, permitiendo así una mejor identificación y respuesta ante ella.

Industrial Control Systems (ICS) were initially designed to work in sealed environments and as stand-alone systems, interconnections between systems were scarce, as were safety protections. The constant evolutions in the field of ICS, including the inclusion of a large number of communication protocols, IIoT devices, the expansion of interconnections, an incessant search for interoperability between systems and the inclusion of these architectures in critical systems, has meant that the networks on which these industrial control systems, has meant that the networks on which these industrial control systems are built, also known as control networks, have increased their security exponentially.

The programming of PLCs is a fundamental part of the initial phases when building and designing industrial plants. About that environment, the company will base all its operations in that environment making the configuration of these controllers a critical element. When it comes to programming these devices there are a series of steps and best practices that take advantage of the native functionalities available and that involve little or no need to resort to a PLC programmer, protecting the device in a simple way with minimum spend on resource.

PLCs, or Programmable Logic Controllers, have been part of industrial environments since the birth of automation. Given their evolution over time, thanks to greater intelligence, they have become a target of interest for potential attackers.

Organisations are exposed to the consequences of cyber threats, and may be ill-prepared to face and manage cyber incidents, whether provoked or unprovoked. For this reason, in 2014 INCIBE launched its Indicators for the Improvement of Cyber Resilience (IMC) model, with the aim of improving and understanding the state of cyber resilience in organisations.

Nobelium es la denominación de Microsoft para un grupo de atacantes que, según la atribución llevada a cabo por la Agencia de Seguridad de Infraestructura y Ciberseguridad (CISA) de Estados Unidos, pertenecen al Servicio de Inteligencia Exterior (SRV) de Rusia. Este grupo criminal es conocido por el ataque a la cadena de suministro de SolarWinds, y una campaña masiva de phishing haciéndose pasar por una empresa de desarrollo estadounidense.

Demilitarized zones, also known as DMZs (demilitarized zones), are used for the secure exchange of information between computers on a network that we want to protect and an external network that needs to access those computers. DMZs are widely used in the IT sector and also in the OT sector, but the equipment and services they host are not exactly the same.

In recent years, the concept of machine learning has gained more prominence, mainly driven by advances in parallel computing capacity. More and more developments, applications and programs are using these algorithms to provide systems with greater security, intelligence and independence. However, it’s rarely used in industrial environments, although some recent tests and developments prove its effectiveness, including in the scope of detection and prediction of cyber attacks.



