Keys to implementing the new vehicle cybersecurity regulations R155 and R156
Posted on 28/11/2024, by
INCIBE (INCIBE)

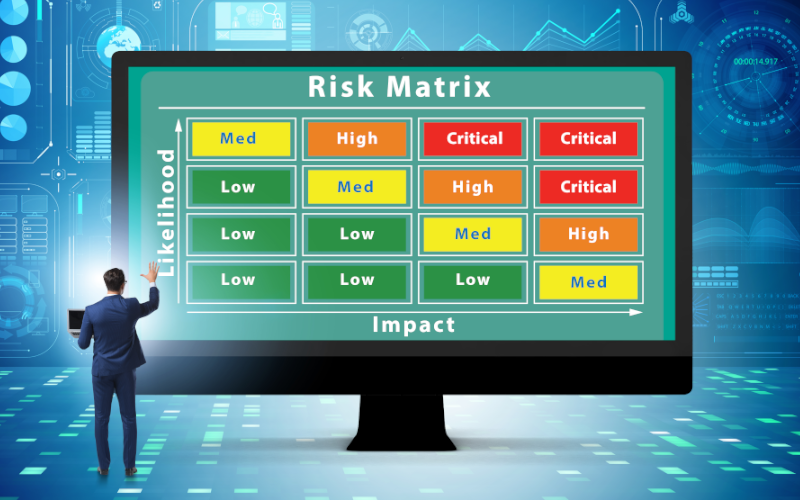
This article aims to present a brief example guide for an implementation of the new standard in a supplier's facilities.Going through the critical points of the standard, a generic use case will be followed to exemplify how a vehicle manufacturer can adapt its processes to comply with the new standard in an efficient and effective way.By presenting an overview of the standard and production processes, the aim is to provide a brief guide to serve as a starting point and help avoid common failures in industrial environments when faced with new regulations, such as redundancy of effort, inefficiency in resource management and deficiencies in the application of safety measures.