
The BACnet (Building Automation and Control Networks) communications protocol is a standardised, open protocol developed by ASHRAE (American Society of Heating, Refrigerating and Air-Conditioning Engineers Inc) designed for smart building management. Its main advantage is the ease with which it enables communication between different devices and systems from various brands.
This article provides a technical analysis of the BACnet protocol, explaining its technical concepts, new features and advantages in industrial environments, and how it has evolved to meet today's cybersecurity requirements.

Today, one of the most critical, but least known, procedures in industrial security is the secure development. This article gathers all the best practices for the creation of specific applications and equipment for industrial environments in a secure manner. Security aspects that must take into account both the work done during the design (confidentiality of the company and customers, workers' security...), and the security that the designed product itself must present throughout its life cycle (vulnerability management, access control, input/output management...).
The aim of this article is to address the good practices of secure development, from the perspective of industrial cybersecurity. Although traditional best practices can be applicable to these environments, the fundamental aspects of safety and availability generate different approaches, mainly in aspects related to memory and resource management, update and patch management cycles, etc.

This article aims to present a brief example guide for an implementation of the new standard in a supplier's facilities.
Going through the critical points of the standard, a generic use case will be followed to exemplify how a vehicle manufacturer can adapt its processes to comply with the new standard in an efficient and effective way.
By presenting an overview of the standard and production processes, the aim is to provide a brief guide to serve as a starting point and help avoid common failures in industrial environments when faced with new regulations, such as redundancy of effort, inefficiency in resource management and deficiencies in the application of safety measures.

A CI/CD (Continuous Integration/Continuous Deployment) pipeline is an essential tool in modern software development, which allows you to automate and optimize the entire development lifecycle, from code integration to its deployment in production. The article aims to explain security in CI/CD pipelines, motivating readers to adopt automated practices that not only optimize software development, but also minimize the associated risks. Keep in mind that automation carries certain risks if not handled safely, as it can increase the attack surface for cybercriminals. It underscores the importance of implementing security controls at every stage of the pipeline, urging developers to take initiative-taking steps to protect their code, their environments, and ultimately, their final products.
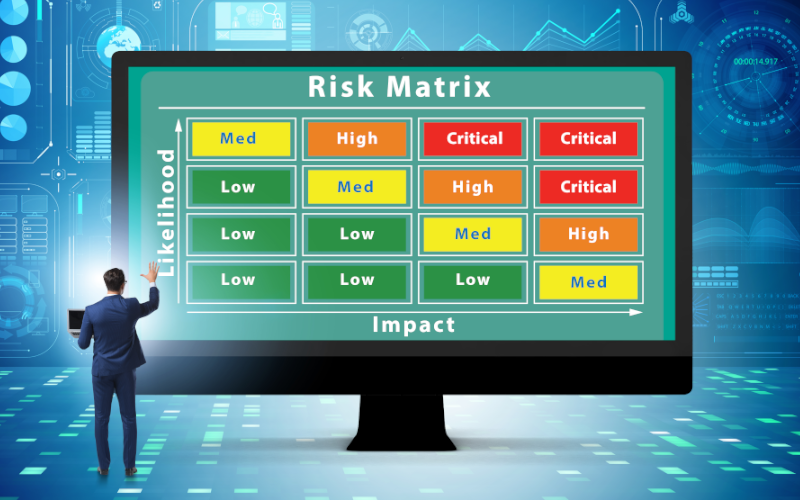
In the era of interconnection and digitization, industrial control systems (ICS) are increasingly exposed to cyber threats. These systems are vital for energy production, manufacturing and critical infrastructure management, and their protection has become an essential priority.
Risk analysis is fundamental in this context, as it allows identifying, assessing and prioritizing the risks that can affect ICS. This process, ranges from technical vulnerabilities to emerging threats, and is crucial for developing effective mitigation and protection strategies.
In this article, the challenges and solutions related to risk analysis in ICS will be explored, as well as the importance of the IEC 62443-3-2 standard in this critical process.
The digital twins are virtual recreations of real-world objects or processes. This innovative idea, proposed by Dr. Michael Grieves, has become increasingly relevant in various industrial sectors thanks to the advancement of technologies such as 3D modelling, the Internet of Things (IoT), the IIoT (Industrial Internet of Things), machine learning and big data. Its application makes it possible to simulate and analyse physical processes efficiently, thus contributing to the digital transformation of industry, also known as Industry 4.0.
The fundamental purpose of digital twins is to facilitate the understanding of how elements operate in the physical world. For example, in manufacturing, it is possible to create a digital twin of a factory and through simulations explore different scenarios: what would happen if a machine were modified, how would it impact production, and what would happen if a machine were changed? The digital twin provides answers before real changes are made to the physical environment, speeding up decision-making and optimising processes.

The agri-food sector is one of the most critical sectors today because it is one of the most important sectors for the country's economy, as it produces food.
This sector, like many others, is in continuous evolution. An example of this is the automation and digitalization of the many processes that are carried out. These new technologies bring many advantages, such as more efficient processes, less water consumption, detection of possible risks, etc. These great advantages also bring with them some problems, such as increased exposure to cyber-attacks.
Therefore, this article provides some basic knowledge to make the industry aware of the importance of implementing cybersecurity in their technologies.
There are currently many standards and regulations in the industrial sector. A wide variety of them allow industrial organizations to check their level of maturity, such as IEC 62443, or to improve the security level of the organization through the application of a series of guidelines, good practices or guides, as in the case of the NIST Framework.
Given the growth of the industrial sector, and the increase in capabilities, both in production and connectivity, thanks to the consolidation of Industry 4.0 and the emergence of Industry 5.0, industrial environments are in the focus, not only of technological improvements, but also of cyber-attacks.
The application and implementation of the IEC 62443 family, in combination with the NIST Framework, will enable organizations to reduce, mitigate and control the possibility of suffering a cyber-attack by implementing the controls and best practices defined in both standards.

UMAS (Unified Messaging Application Services) is a Schneider Electric (SE) proprietary protocol used to configure and monitor Schneider Electric programmable logic controllers (PLCs). While it is true that the protocol is related to this manufacturer, the use of the protocol is quite widespread in different sectors, especially the energy sector, as is obvious.
The article will focus on the technical breakdown of the protocol and the use of the protocol. The article will also show weaknesses, strengths and some technical vulnerabilities detected in this protocol.
The UN R155 and UN R156 regulations are of vital importance for vehicle cybersecurity. From July 2022, all car manufacturers that want to be type-approved must comply with both regulations, but from July 2024 this requirement will be extended to all new vehicles sold in the European Union, regardless of when the manufacturer obtained type-approval. One of the most important aspects of compliance with both regulations is the completion of a cybersecurity risk assessment of the vehicle, including all integrated components of the vehicle's supply chain. On the other hand, it also specifies how to incorporate cybersecurity from design, how to detect and respond to incidents, how to securely update vehicle software, etc.



