
In the electricity sector, it has always been necessary to use robust communications that allow proper communication, since a failure in this sector would cause a large number of losses, both economic and social.
In addition, with the technological advances, it is important also to have secure communications since the electricity sector is one of the sectors that currently suffers the most cyber-attacks. For this reason, in recent years different robust and secure protocols have been created.
One of these protocols is DNP3, created mainly for the use of substation automation and control systems, for the electric utility industry, although it has now also been used for other sectors.
Finally, in this article we want to explain in more depth the operation of this protocol and the benefits or disadvantages of using this protocol.

CAPEC (Common Attack Pattern Enumeration and Classification) is a project that focuses on enumerating and classifying common attack patterns on computer systems and providing a systematic approach to understanding and addressing the tactics used by attackers. Like CWE (Common Weakness Enumeration), CAPEC is an initiative of the computer security community and is maintained by the National Institute of Standards and Technology (NIST) in the United States. Recently in version 3.9, the project has incorporated a number of attack patterns related to the industrial world.
This article aims to show the reader the use of these codes, such as those used at the identifier level in CVEs, CWEs, etc., and which are related to many of the jobs that are carried out on a daily basis in the industrial cybersecurity sector.

The automotive sector is currently moving towards electric consumption, as society is becoming more and more aware of the problems that environmental pollution can cause.
One of the big challenges of this trend is how to charge electric vehicles, for which charging points are currently used.
But like most of today's technological devices, they will also need to have access to an Internet connection in order to be able to monitor in real time the use of the station, the customer's banking information, etc.
For this reason, in this article we want to talk about the different risks or cyber-attacks that these charging points may suffer and the problems they may cause, as this is a very important sector for society and one that is capable of managing very sensitive information

External access provides great convenience to workers, as it allows them to access any industrial equipment deployed in the field from the office or even further away. However, this type of access can pose a number of security problems for the company. This article reviews the main problems and how to solve them.

The Industrial Internet of Things (IIoT) has experienced considerable growth in recent years, providing crucial improvements. However, it also has some limitations in terms of consumption, security, cost or scalability. In this blog, we will see how the appearance of LoRaWAN in this area can solve part of those limitations.

The TETRA (Terrestrial Trunked Radio) network is a standard developed in Europe in the 1990s by ETSI (European Telecommunications Standards Institute), whose emergence came because of the management of telephone communications for extreme cases, in which standard communication via mobile might not work properly. Therefore, it can be considered as an alternative network for communications with emergency and security services to be always operational. TETRA unifies different digital radio interface alternatives for communications and serves as a standard for the construction of private mobile networks or PMR (Private Mobile Radio).
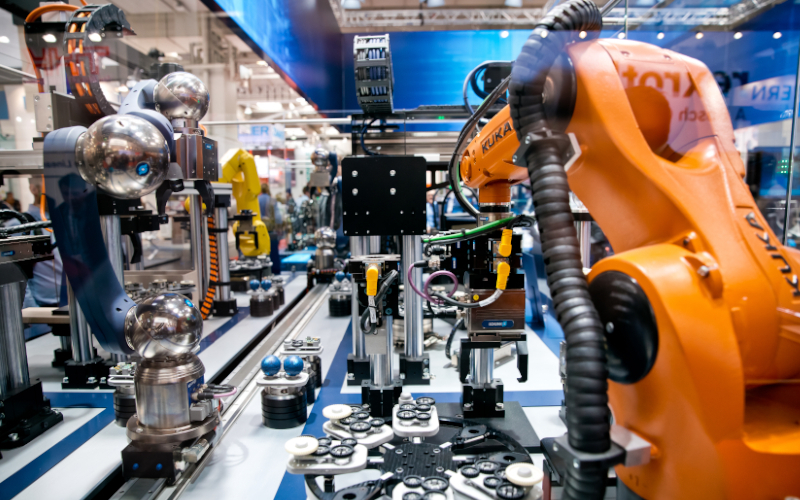
Within the industrial world, there are some sectors such as robotics, which has evolver considerably. This has led to the need to update all the regulations and standards, both in terms of physical (safety) and cybersecurity. (security). Given that the robotics sector is and will increasingly become a highly technical sector with exponential growth, the need to update all documentation has been promoted by a large group of companies in the sector, which, above all, have focused their concerns on the cybersecurity of the industrial robotics world.

Knowing the resources available when performing tasks of hardening a system, will allow us to optimize the time necessary to obtain a safer system. In addition, we have the possibility of using tools capable of auditing the system that identifies those configurations that are considered safe and which ones we could implement.

In industrial environments there are a multitude of technologies, manufacturers, communications, etc. This article will reflect a small part of the protocols that use radio frequency (RF) communications. Thanks to these wireless communications, operators in the industrial world can send a simple order to obtain information on the status of a sensor or execute control orders in the industrial environment. The importance of a good implementation, in terms of cybersecurity of these communications, is quite high since, on occasions, some of the attacks that have been investigated have an impact on the physical world, giving rise to incidents that can even result in fatalities.




