
The increasing development of malware targeting the industrial world has not halted its momentum in the slightest. Several research groups have detected a new malware called Fuxnet and are currently investigating its scope. This malware has the capability to send specific requests at the serial level, via RS485/MBus, executing floods to more than 87.000 assets, including control systems and integrated sensors deployed across different sectors. Among the infrastructures compromised by this malware, we find hospitals, airports and other critical infrastructures that provide essential services to the population.
MITRE Caldera OT stands out mainly for being an open-source tool that allows the simulation of different cyber-attacks in industrial environments. This tool was created by MITRE and CISA (US Cybersecurity and Infrastructures Security Agency), as the experts saw the need to be able to improve and understand cybersecurity in industrial environments without using a high number of resources.
In addition, this tool is designed to be used by both the Red Team and the Blue Team, allowing both teams to collaborate with each other to improve the level of cyber security in these environments.
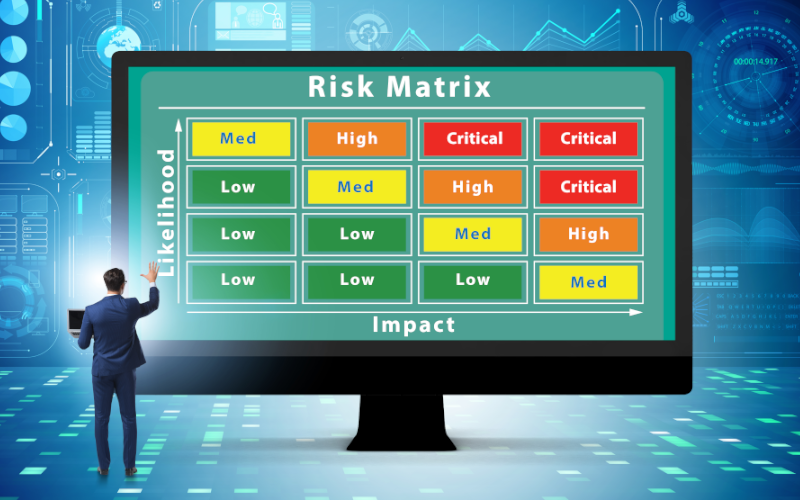
In the era of interconnection and digitization, industrial control systems (ICS) are increasingly exposed to cyber threats. These systems are vital for energy production, manufacturing and critical infrastructure management, and their protection has become an essential priority.
Risk analysis is fundamental in this context, as it allows identifying, assessing and prioritizing the risks that can affect ICS. This process, ranges from technical vulnerabilities to emerging threats, and is crucial for developing effective mitigation and protection strategies.
In this article, the challenges and solutions related to risk analysis in ICS will be explored, as well as the importance of the IEC 62443-3-2 standard in this critical process.
The digital twins are virtual recreations of real-world objects or processes. This innovative idea, proposed by Dr. Michael Grieves, has become increasingly relevant in various industrial sectors thanks to the advancement of technologies such as 3D modelling, the Internet of Things (IoT), the IIoT (Industrial Internet of Things), machine learning and big data. Its application makes it possible to simulate and analyse physical processes efficiently, thus contributing to the digital transformation of industry, also known as Industry 4.0.
The fundamental purpose of digital twins is to facilitate the understanding of how elements operate in the physical world. For example, in manufacturing, it is possible to create a digital twin of a factory and through simulations explore different scenarios: what would happen if a machine were modified, how would it impact production, and what would happen if a machine were changed? The digital twin provides answers before real changes are made to the physical environment, speeding up decision-making and optimising processes.

Durante este artículo indagaremos en el funcionamiento y objetivos de una nueva tecnología de nueva adopción en el campo de la ciberseguridad, consistente en la creación de señuelos o información engañosa dentro de un Sistema de Control Industrial, permitiendo detectar y retrasar la intrusión de un ciberatacantes en un tiempo menor.

The agri-food sector is one of the most critical sectors today because it is one of the most important sectors for the country's economy, as it produces food.
This sector, like many others, is in continuous evolution. An example of this is the automation and digitalization of the many processes that are carried out. These new technologies bring many advantages, such as more efficient processes, less water consumption, detection of possible risks, etc. These great advantages also bring with them some problems, such as increased exposure to cyber-attacks.
Therefore, this article provides some basic knowledge to make the industry aware of the importance of implementing cybersecurity in their technologies.

Today, rail transport is a key strategic sector, both for the transport of people and goods of all kinds. It is also a sector in constant evolution and progress, which has adopted new technologies, from Wi-Fi zones for employees and customers, to new remote distributed control technologies, GPS and IoT.
While all applied technologies provide many advantages, they can also bring problems and introduce cybersecurity risks. The objective of this article will be to raise awareness of some of the most important cyber-attacks that have occurred in the industry and to contribute to the general awareness of the evolution of railway cybersecurity and cyber-attack protection measures available to the industry.

In the industrial environment, the interconnection of industrial equipment for maintenance via the Internet is becoming increasingly common. However, this has also opened the door to a new and dangerous landscape of threats. This article reviews one of the most representative threats within this current new paradigm, APTs, how concern about this type of threat is increasing, and how they operate during an industrial attack.
There are currently many standards and regulations in the industrial sector. A wide variety of them allow industrial organizations to check their level of maturity, such as IEC 62443, or to improve the security level of the organization through the application of a series of guidelines, good practices or guides, as in the case of the NIST Framework.
Given the growth of the industrial sector, and the increase in capabilities, both in production and connectivity, thanks to the consolidation of Industry 4.0 and the emergence of Industry 5.0, industrial environments are in the focus, not only of technological improvements, but also of cyber-attacks.
The application and implementation of the IEC 62443 family, in combination with the NIST Framework, will enable organizations to reduce, mitigate and control the possibility of suffering a cyber-attack by implementing the controls and best practices defined in both standards.




